|
4G/LTE - APN |
||
|
APN Request/Assignment in ePDG
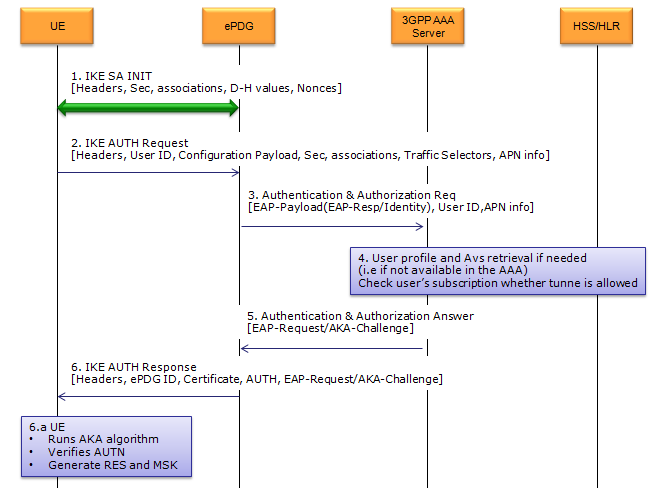
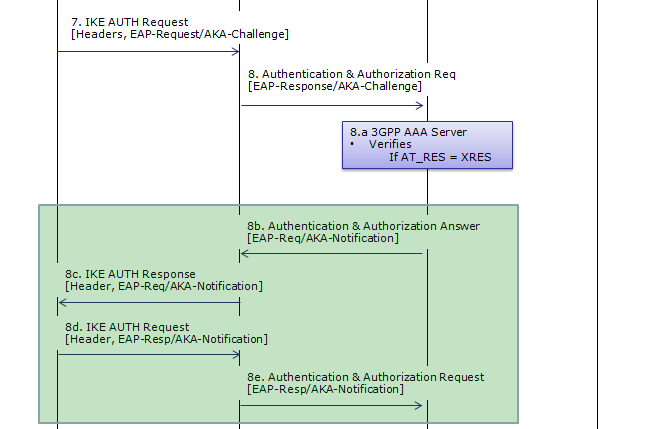
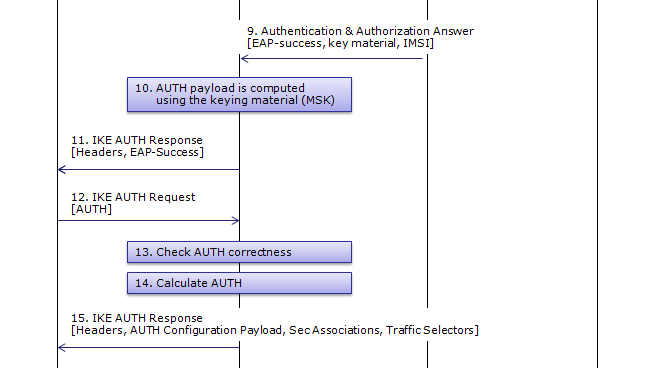
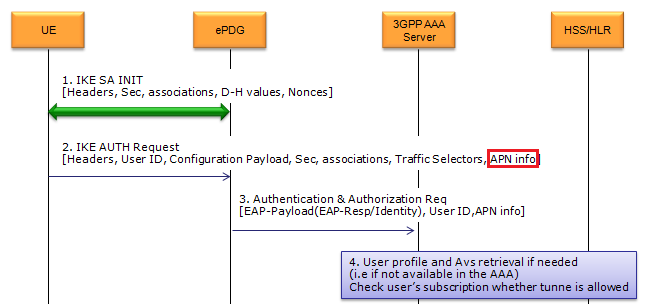
UE IP allocation and various server IP can be assinged to UE over ePDG. This IP allocation happens during the IKE process when UE first go through ePDG. Overall IKE(key exchanging) protocol sequence in 33.402 is as shown below. (This is from Figure 8.2.2-1). Don't bother looking into each of these steps, only two of the steps in this sequence gets involved in the APN Request/Allocation. The simpler version of sequence will be shown after this figure. (If you are really interested in the details of each of these steps, refer to IKE page)
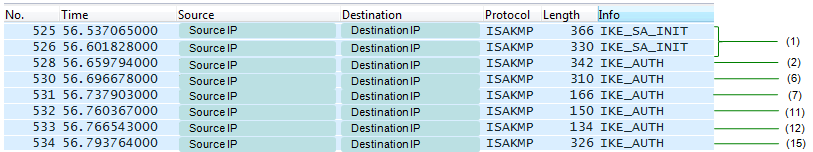
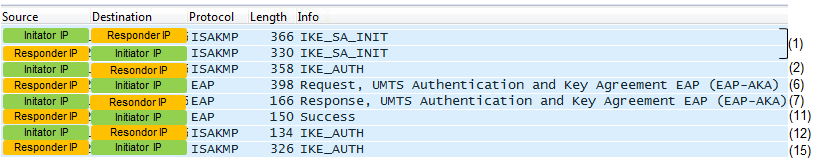
If you have the IP log at the UE and WiFi AP, you may see only following part (the steps happening at core network parts will not be captured at this terminal log). I put the step number in parethesis to match each line on the wireshark to the step number in the figure shown above. This is ISAKMP log that is not decoded. So you would not get the full details from this log except step (1).
If you managed to decode the whole ISAKMP packet including the Encrypted Payload part, you will see the wireshark log as shown below.
If I point out the message that carries APN Info, it is shown as follows.
Example 1 >
CFG Request (in Step 2 ) ------------------------------------------------------------------------
Internet Security Association and Key Management Protocol Initiator SPI: 63b6607c34cf9e41 Responder SPI: aaaaaaaaaaaaaaaa Next payload: Encrypted and Authenticated (46) Version: 2.0 0010 .... = MjVer: 0x02 .... 0000 = MnVer: 0x00 Exchange type: IKE_AUTH (35) Flags: 0x08 (Initiator, No higher version, Request) .... 1... = Initiator: Initiator ...0 .... = Version: No higher version ..0. .... = Response: Request Message ID: 0x00000001 Length: 428 Type Payload: Encrypted and Authenticated (46) Next payload: Identification - Initiator (35) 0... .... = Critical Bit: Not Critical Payload length: 400 Initialization Vector: 2e25ced9813fef344057cd7c1284b750 (16 bytes) Encrypted Data (368 bytes) Decrypted Data (368 bytes) Contained Data (351 bytes) Type Payload: Identification - Initiator (35) Next payload: Identification - Responder (36) 0... .... = Critical Bit: Not Critical Payload length: 80 ID type: ID_RFC822_ADDR (3) Protocol ID: Unused Port: Unused Identification Data:0001010123456789@5C-A4-8A-1F-59-50 :nai.epc.mnc001.mcc001.3gppnetwork.org ID_FQDN: 0001010123456789@5C-A4-8A-1F-59-50 :nai.epc.mnc001.mcc001.3gppnetwork.org Type Payload: Identification - Responder (36) Next payload: Configuration (47) 0... .... = Critical Bit: Not Critical Payload length: 11 ID type: KEY_ID (11) Protocol ID: Unused Port: Unused Identification Data: ID_KEY_ID: 696d73 ==> ims Type Payload: Configuration (47) ....
|
||