|
Security Overview
Let's suppose two parties try to communicate each other and at the same time they don't want those communication being hacked by others in any way.
Just in terms of communication method, they can use roughly two different method.
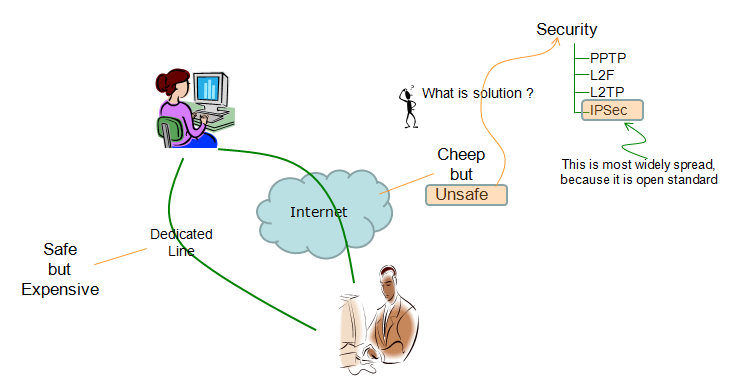
One is to use a dedicated line which is open only to the two parties. Communication over this path can safely protected since it is extremly difficult for any intruder to sniff into this kind of path. However, as you may easily guess.. it would be very expensive especially when those two parties are located geographically very far from each other.
Another way of communication would be to use the existing internet which is almost everywhere. Since all the physical path is already there, you can communicate each other with almost no cost. But the problem is that anybody can easily hijack the communication and use it for malicious purpose. Simply put, we can say "Communication over Internet" can be "Unsafe"
or "In-Secure".
What do you want to keep secure ?
Ideally you may want to keep everything you want to exchange over the internet, but roughly we may group them into a few separate categories as below :
- Information about authentication : Typical examples are password and user id
- User traffic data : This includes any user traffic that you want to protect like financial transaction, personal information etc.
Algorithms / Components of IP Security
Then you may ask "Is there any way to use such a open/cheep media but keep all the communication securely protected at the same time ?". That's the motivation of 'Security' algorithms...
There are various kinds of methods and algorithms for IP Security, but we can classifies them into a few categories as folls :
- Authentication Algorithm : This is to ensure that the sender and reciever are really those who are supposed to be. Some of the typtical examples are :
- Message Authentication Codes (MACs): This is used to verify the integrity of a message and ensure that it has not been tampered with during transmission. A few examples are HMAC (Hash-based Message Authentication Code) and CMAC (Cipher-based Message Authentication Code), AH (Authentication Header) etc.
- Digital Signatures: This is used to provide non-repudiation and verify the authenticity of a message. A few examples are RSA (Rivest-Shamir-Adleman) and DSA (Digital Signature Algorithm).
- Public Key Infrastructure (PKI): This is a system that uses digital certificates and a hierarchical system of trusted entities to authenticate the identity of users and devices. A few examples are X.509 and SSL/TLS certificates
- Encryption Algorithm : This is used to scramble the data in transit, making it unreadable to anyone who intercepts it. There are two types of encryption algorithms:
- Symmetric Encryption: This uses the same key to encrypt and decrypt the data. A few examples are AES (Advanced Encryption Standard), DES (Data Encryption Standard), and 3DES (Triple DES).
- Asymmetric Encryption: Asymmetric encryption uses two different keys, a public key and a private key, to encrypt and decrypt the data. Some examples are RSA (Rivest-Shamir-Adleman), Elliptic Curve Cryptography (ECC), DSA (Digital Signature Algorithm), ElGamal, GPG (GNU Privacy Guard), PGP (Pretty Good Privacy).
- Key Management Algorithm: This is used to generate and distribute keys used for encryption and authentication. There are several types of key management algorithms as follows :
- Key Generation Algorithms: This is used to generate random keys for encryption and authentication. A few examples are AES key generation and RSA key generation.
- Key Exchange Algorithms: This is used to securely exchange keys between two parties. A few examples are Diffie-Hellman and Elliptic Curve Diffie-Hellman (ECDH).
- Key Distribution Algorithms: This is used to securely distribute keys to the intended recipients. A few examples are the Key Distribution Center (KDC) used in Kerberos authentication and the Public Key Infrastructure (PKI) used in SSL/TLS encryption.
The security algorithm specially designed for IP layer communication is called 'IPSec'.
IPSec has three major subfields as shown below. Each of these fields will be the topic for this posts.
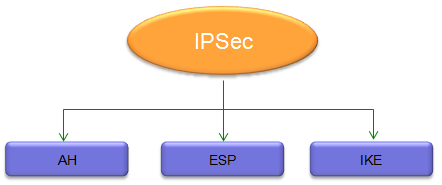
Technically AH and ESP are the algorithm designed for IPSec and IKE is a kind of protocol that is used to exchange secrete keys which will be used for AH/ESP algorithm. So AH/ESP and IKE has a little bit different functionality.
Recommended Video :
Engma Simulator
|

