|
|
||
|
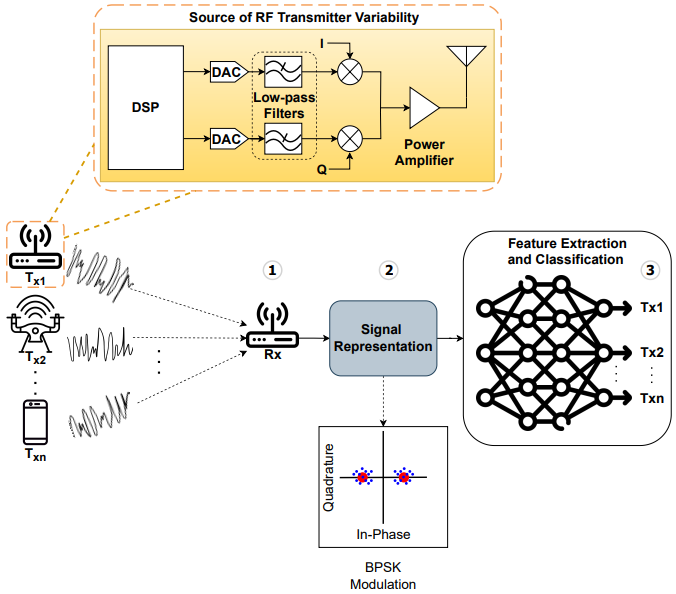
Radio fingerprinting is a technique used to uniquely identify wireless transmitters based on their inherent hardware imperfections. Every radio device, even those of the same model and manufacturer, exhibits slight variations in components such as digital-to-analog converters, filters, and power amplifiers. These imperfections introduce subtle, unique distortions in the transmitted signal, forming a distinctive signature that can be captured and analyzed. By processing received signals and extracting key features, machine learning or signal processing algorithms can classify and authenticate transmitters based on their unique fingerprints. This method is widely applied in areas such as wireless security, fraud detection, spectrum management, and device authentication, offering a reliable way to distinguish between trusted and potentially unauthorized transmitters. System OverviewRadio fingerprinting is a technique used to distinguish individual wireless transmitters based on their unique hardware-induced signal variations. Even transmitters of the same make and model exhibit slight imperfections in components such as digital-to-analog converters (DACs), filters, and power amplifiers, leading to subtle distortions in their transmitted signals. By capturing these signals at a receiver and analyzing their distinct characteristics, a machine learning model can classify and identify the source transmitter. This approach is particularly useful in security applications, spectrum monitoring, and network authentication, providing a robust method to verify the authenticity of wireless devices. Radio fingerprinting leverages the inevitable hardware variations in wireless devices to create a unique identifier for each transmitter. By capturing, representing, and classifying signals, this system provides a powerful tool for secure and reliable wireless communications. The combination of signal processing and machine learning ensures high accuracy in identifying individual transmitters, making it a valuable technology in modern wireless security and spectrum monitoring applications. Following diagram shows an example of overall architecture of a radio fingerprinting system. The radio fingerprinting system consists of several key stages, as illustrated below. RF signal transmission, signal reception and representation, and feature extraction with classification. These steps ensure that the transmitter's unique characteristics are captured, processed, and used for identification.
Image Source : Radio Frequency Fingerprinting via Deep Learning: Challenges and Opportunities Followings are breakdown of the system and descriptions. RF Signal Transmission and VariabilityRF signal transmission and variability play a critical role in enabling unique identification of transmitters, such as Tx1, Tx2, ..., Txn, through the generation of wireless signals shaped by each transmitter's distinct hardware configuration. As the transmitted signal undergoes processing, it is influenced by slight distortions introduced by hardware imperfections in components like the Digital Signal Processor (DSP), Digital-to-Analog Converter (DAC), Low-Pass Filters, and Power Amplifiers, which introduce variations in amplitude, phase, frequency response, noise, and nonlinearities. These hardware-induced variations collectively create a unique signal fingerprint for each transmitter, forming the basis for advanced signal identification and localization techniques in wireless communication systems.
Signal Reception and RepresentationSignal reception and representation are essential processes in wireless communication, where a receiver (Rx) captures signals from multiple transmitters within range, transforming them into a structured form often represented by in-phase (I) and quadrature (Q) components. This phase-space representation facilitates the analysis of subtle distortions, enabling transmitter fingerprinting by highlighting unique characteristics in the signals. The system frequently employs modulation techniques such as Binary Phase Shift Keying (BPSK), where slight shifts in the constellation points reflect transmitter-specific traits, providing a foundation for advanced identification and localization in wireless networks.
Feature Extraction and ClassificationFeature extraction and classification are pivotal in advanced wireless communication systems, where the signal representation, derived from received transmissions, is analyzed by a machine learning-based classification system. Utilizing neural networks or traditional signal processing techniques, unique features are extracted from the signals, enabling the identification of specific transmitters (Tx1, Tx2, ..., Txn) by distinguishing between different sources. This classification process supports critical applications such as device authentication—ensuring only authorized transmitters communicate within a network—intrusion detection by identifying rogue or spoofed transmitters, and network security monitoring to detect anomalies in wireless communications, thereby enhancing the security and reliability of wireless networks.
Use CasesRadio fingerprinting has a wide range of practical use cases across various domains. These use cases demonstrate radio fingerprinting’s versatility, leveraging its ability to provide unique, hardware-based identification to enhance security, efficiency, and reliability across a broad spectrum of wireless applications. Incorporating RFF into these areas leverages the unique physical-layer attributes of wireless devices, providing an additional layer of security and management capabilities beyond traditional software-based methods. Device Authentication and SecurityDevice authentication and security are critical in modern wireless networks, where radio frequency fingerprinting (RFF) plays a pivotal role in preventing device cloning and enhancing overall security. By detecting cloned devices that attempt to mimic legitimate ones through identifying discrepancies in their unique signal characteristics, RFF ensures robust identification at the physical layer, adding an extra layer of protection that makes unauthorized access significantly more difficult, thereby safeguarding network integrity and reliability.
Spectrum Management and Interference MitigationRadio Frequency Fingerprinting (RFF) plays a critical role in enhancing spectrum management and mitigating interference, offering powerful tools for regulatory bodies and network operators. One key application is identifying unauthorized transmitters—RFF enables regulators to pinpoint illicit or rogue transmissions that may disrupt licensed spectrum usage, allowing for swift intervention to mitigate interference and ensure compliance with regulations. Additionally, RFF supports efficient spectrum allocation by distinguishing between different transmitters based on their unique signal characteristics. This capability allows for more precise monitoring and management of spectrum resources, optimizing their use, reducing congestion, and improving overall network performance in an increasingly crowded radio frequency environment.
Internet of Things (IoT) Device ManagementRadio Frequency Fingerprinting (RFF) is transforming the management of Internet of Things (IoT) devices, addressing the unique challenges posed by their widespread adoption. One of its primary applications is authenticating IoT devices—by leveraging the distinct RF signatures of each device, RFF ensures that only authorized devices can communicate within a network, significantly enhancing security and preventing unauthorized access or spoofing. Additionally, RFF enables monitoring of device behavior by tracking and analyzing the RF patterns of IoT devices over time. This capability allows for the detection of anomalies that may signal malfunctions, performance degradation, or potential security breaches, enabling proactive maintenance and safeguarding the integrity of IoT ecosystems in smart homes, industrial systems, and beyond.
Military and Defense ApplicationsRadio Frequency Fingerprinting (RFF) is a vital technology in military and defense operations, offering advanced capabilities for enhancing security and intelligence. One key application is identifying friend or foe—by analyzing the unique signal fingerprints of RF transmissions, RFF enables military forces to distinguish between allied communications and potentially hostile ones, improving operational safety and decision-making on the battlefield. Additionally, RFF plays a crucial role in Signals Intelligence (SIGINT), where military agencies use it to monitor, identify, and classify transmissions from specific devices or systems. This enhances situational awareness, supports threat detection, and provides critical insights into enemy activities, making RFF an indispensable tool in modern defense strategies.
Fraud Detection in Wireless CommunicationsFraud detection in wireless communications is essential for maintaining the integrity of secure networks, and radio frequency fingerprinting (RFF) serves as a powerful tool in this domain. By identifying and preventing unauthorized devices from accessing secure communication channels, RFF ensures that only legitimate devices can operate within the network, while its ability to recognize the unique signal characteristics of authorized devices enables it to detect and block spoofed signals attempting to impersonate them, effectively mitigating spoofing attacks and enhancing overall network security.
Enhancing Privacy in Smart Home DevicesRadio Frequency Fingerprinting (RFF) is a powerful tool for bolstering privacy and security in smart home environments, where interconnected devices handle sensitive user data. One key benefit is preventing unauthorized monitoring—RFF can detect and block rogue or unauthorized devices attempting to connect to smart home networks by recognizing their unique RF signatures, thereby safeguarding users from potential eavesdropping or data interception. Additionally, RFF ensures data integrity by authenticating devices at the physical layer, confirming that communications originate from trusted sources. This physical-layer verification reduces the risk of data manipulation or spoofing, providing smart home users with greater confidence in the privacy and reliability of their connected ecosystems.
ChallengesRadio Frequency Fingerprinting (RFF) is a technique that identifies wireless devices based on unique hardware-induced imperfections in their transmitted signals. While RFF offers promising applications in security and device authentication, its practical deployment faces several challenges. The list shown here is based on the paper : Radio Frequency Fingerprinting via Deep Learning: Challenges and Opportunities and it will be extended as I will learn further. Model Interpretability IssuesDeep learning (DL)-based radio fingerprinting models often function as "black boxes," making it difficult to understand the specific features they use for classification. This lack of transparency is particularly concerning in security applications like device authentication and intrusion detection. Understanding the decision-making process is crucial to mitigate false predictions and enhance system robustness.
Lack of Benchmark DatasetsUnlike fields such as computer vision and natural language processing, RFF lacks standardized benchmark datasets. Researchers often rely on locally generated datasets, which may not encompass the full range of real-world deployment conditions. This limitation affects the robustness and generalizability of DL-based RFF models.
Receiver Hardware BiasMost RFF solutions assume that the receiver hardware does not introduce variability into the captured RF fingerprints. However, real-world deployments involve hardware-specific variations, causing models trained on one receiver to be biased toward that specific receiver.
Scalability IssuesAs the number of devices in a network increases, distinguishing between similar RF fingerprints becomes increasingly difficult. This issue is particularly evident in networks using simple modulation schemes like BPSK, where overlapping feature spaces degrade classification performance.
Protocol DependencyCurrent DL-based RFF systems are sensitive to variations in communication protocol configurations. Changes in parameters such as modulation schemes, bit rates, and transmission power can alter the RF fingerprint, leading to reduced system performance when training and testing data differ.
Detection of Unauthorized DevicesMany RFF systems operate under closed-set classification, meaning they can only recognize devices from their training set. This limitation makes them ineffective at identifying previously unseen or unauthorized devices.
Simultaneous TransmissionsIn real-world environments, multiple devices often transmit on the same or nearby frequency channels simultaneously. This overlap can distort the received signals and reduce the accuracy of RF fingerprinting.
Deployment on Constrained DevicesRFF models are often computationally expensive, making them difficult to deploy on lightweight or resource-constrained devices like IoT sensors. Optimized models are required to balance performance and efficiency.
Variable Input LengthWireless signals vary in size and duration depending on the communication protocol. Traditional DL models require fixed-size inputs, so variable-length signals must be truncated or padded, potentially leading to information loss and increased computational overhead.
System AdaptivenessWireless networks are dynamic, with devices frequently joining and leaving. Existing RFF systems assume a static device set, requiring expensive retraining whenever new devices enter the network.
Inference TimeMany RFF systems require real-time processing for security and authentication applications. However, long inference times can make these systems impractical for rapid decision-making.
Robustness to Channel VariationsWireless channels experience environmental fluctuations, multipath effects, and noise, leading to changes in received signal characteristics. This variation degrades the accuracy of DL-based RFF systems, as the training and deployment environments may not match.
JammingMalicious entities can launch jamming attacks by transmitting interference on the same frequency, preventing RFF from accurately extracting device fingerprints.
SpoofingAttackers can eavesdrop on and manipulate RF signals to impersonate legitimate devices. This poses a significant security risk, as an adversary can use modified signals to bypass authentication mechanisms.
Adversarial AttacksDL models used in RFF systems are susceptible to adversarial attacks, where slight modifications to RF signals can mislead the model into incorrect classifications.
Reference :
YouTube
|
||