|
|
||
|
5G Security mechanism is not completely new design comparing to 4G Security mechanism. But there are some differences and improvement in 5G in terms of security protection mechanism. 5G offers several improvements over 4G in terms of security, including stronger encryption, better authentication, and more flexibility in terms of network slicing and virtualization. However, as with any new technology, there are also new security risks that need to be addressed.
What is the problem with Previous Technology ?It seems there is some degree of improvement in every new neneration of cellular communication. The improvement usually comes from compensating the issues in previous technology. I thought it would be good to briefly summarize on what kind of issues were there in previous technology. 2G:
3G:
4G:
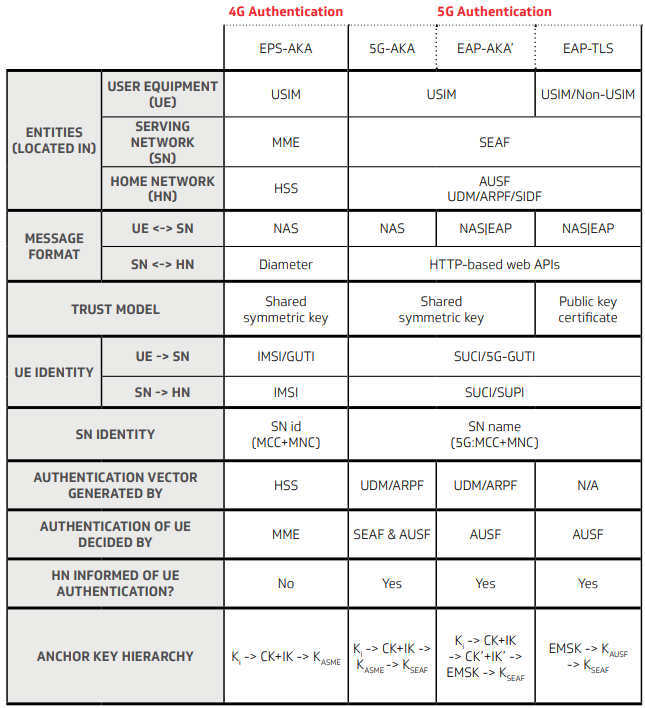
4G vs 5G SecurityThe comparison between 4G and 5G security highlights significant advancements in 5G, driven by the need to address 4G’s vulnerabilities and support a broader range of applications, such as IoT and critical infrastructure. 5G introduces enhanced user authentication and stronger data authentication through new protocols like 5G-AKA, EAP-AKA', and EAP-TLS, which improve upon 4G’s EPS-AKA. Key improvements include better privacy with encrypted identifiers (SUCI), support for public key cryptography, a more distributed security architecture with entities like SEAF and AUSF, and modern communication protocols like HTTP-based APIs. These changes make 5G more secure, scalable, and adaptable to modern threats and use cases.
Authentication Protocols in 5GAuthentication protocols in mobile networks have evolved significantly from 4G to 5G to address security challenges and support diverse use cases. In 4G LTE networks, the EPS-AKA (Evolved Packet System-Authentication and Key Agreement) protocol serves as the standard for authenticating users and establishing secure communication using a shared symmetric key. 5G introduces more advanced protocols, with 5G-AKA as the primary method, building on EPS-AKA to enhance security and privacy while maintaining compatibility. Additionally, 5G supports EAP-AKA', an extensible authentication protocol variant often used for non-3GPP access like Wi-Fi, and EAP-TLS, a certificate-based protocol that leverages public key cryptography to provide stronger security, particularly for scenarios requiring higher trust and integrity. These advancements in 5G authentication protocols ensure greater flexibility, privacy, and resilience against modern threats compared to 4G.
Why These Changes MatterThe improvements in 5G security are driven by the need to address 4G’s vulnerabilities and support 5G’s broader use cases (e.g., IoT, critical infrastructure, ultra-low latency applications). Here’s why each change is significant:
Comparative Table between 4G and 5GThe comparison table between 4G and 5G security provides a high-level overview of the advancements in 5G, focusing on key areas such as entities involved, message formats, trust models, identity management, authentication processes, and key hierarchies. It contrasts 4G’s EPS-AKA protocol with 5G’s authentication methods—5G-AKA, EAP-AKA', and EAP-TLS—highlighting how 5G improves user and data authentication through enhanced privacy, modern protocols, and more robust cryptographic mechanisms, making it better suited for diverse and demanding applications like IoT and critical infrastructure.
Source : 4G vs 5G Security, The Key Differences - CableLabs Followings are breakdown of the table and description. It is just verbalized form of the table. This row identifies the network entities involved in authentication and their roles in 4G and 5G networks.
This row describes the protocols used for communication between entities.
This row describes the cryptographic foundation of authentication. Symmetric key systems (used in 4G and 5G-AKA/EAP-AKA') rely on securely distributing and storing the shared key, which can be a vulnerability if the key is compromised. EAP-TLS’s public key cryptography eliminates this risk by using certificates, which are harder to forge and don’t require pre-shared secrets. This makes EAP-TLS more secure, especially for non-3GPP access (e.g., Wi-Fi).
This row explains how the UE identifies itself to the network. 5G’s use of SUCI addresses a major privacy flaw in 4G, where IMSI catchers (fake base stations) could intercept the IMSI and track users. By encrypting the SUPI into a SUCI, 5G ensures that the permanent identifier is protected during transmission, significantly enhancing user privacy.
This row describes how the serving network identifies itself. The change is mostly syntactic, but the explicit “SN name” in 5G aligns with its service-based architecture, where entities are identified in a more standardized way.
This row explains which entity generates the authentication vectors (sets of cryptographic values used to authenticate the UE). In 5G, the UDM/ARPF takes over the role of generating authentication vectors, aligning with the new architecture. EAP-TLS skips this step entirely, as it relies on certificate-based authentication, which doesn’t require pre-generated vectors.
This row indicates which entity decides if the UE is authenticated. In 4G, the MME (in the serving network) has full control over authentication, which can be a point of failure if the serving network is compromised. 5G distributes this responsibility (in 5G-AKA) or shifts it to the home network (in EAP-AKA' and EAP-TLS), reducing the risk of a compromised serving network affecting authentication.
This row checks if the home network is informed of the UE’s authentication status. In 4G, the lack of home network involvement means it has no visibility into whether the UE was successfully authenticated, limiting accountability. 5G ensures the home network (via the AUSF) is aware, improving oversight and enabling better detection of fraudulent activity.
This row describes the hierarchy of keys used to secure communication. 5G introduces a more granular key hierarchy, with separate keys for the SEAF and AUSF, improving key separation and reducing the impact of a compromised key. EAP-TLS's use of EMSK aligns with its certificate-based approach, providing a stronger cryptographic foundation.
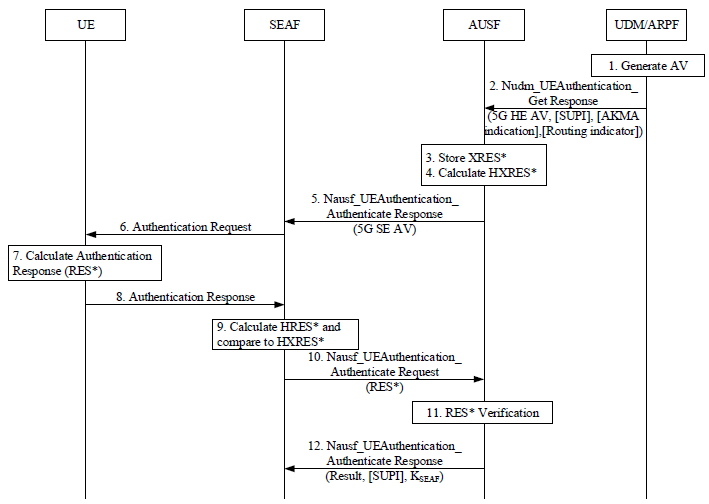
5G Authentication ProcessThe 5G-AKA authentication process ensures mutual authentication: the UE verifies the network’s authenticity (via AUTN), and the network verifies the UE (via RES* comparison). It also establishes the anchor key K_SEAF for secure communication. The use of SUCI/SUPI protects user privacy, and the distributed roles of SEAF, AUSF, and UDM/ARPF enhance security by separating responsibilities across the network. This process is more robust than 4G’s EPS-AKA, with better privacy and key derivation mechanisms. The diagram below illustrates the 5G authentication process using the 5G-AKA (Authentication and Key Agreement) protocol. It outlines the steps and interactions between four key entities in a 5G network: the User Equipment (UE), the Security Anchor Function (SEAF), the Authentication Server Function (AUSF), and the Unified Data Management/Authentication Credential Repository and Processing Function (UDM/ARPF). The process ensures mutual authentication between the UE and the network, establishes shared keys for secure communication, and protects user privacy through encrypted identifiers. < 33.501-Figure 6.1.3.2-1: Authentication procedure for 5G AKA >
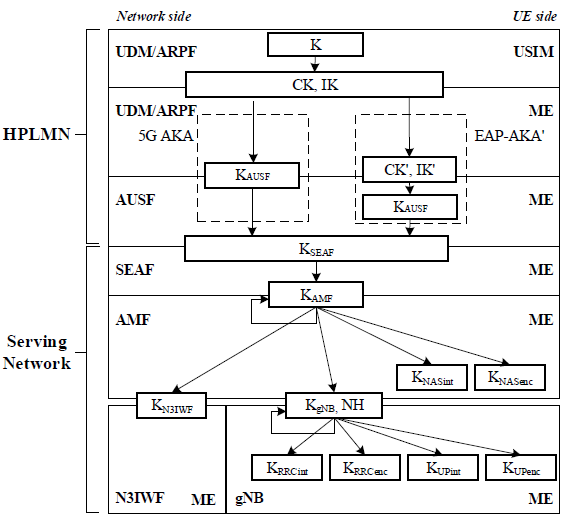
Key Hierarchy and DistributionKey hierarchy and distribution in 5G are fundamental to ensuring secure communication, authentication, and data integrity across the network. The system follows a structured and hierarchical key derivation mechanism, where a root key, stored securely in the USIM, serves as the foundation for generating multiple security keys. These keys are derived and distributed across various network entities, including the Authentication Server Function (AUSF), Security Anchor Function (SEAF), Access and Mobility Management Function (AMF), and the gNB, ensuring that each layer of the network has the necessary cryptographic protections. The hierarchical nature of the key system ensures that if a lower-level key is compromised, the root key remains protected, preventing unauthorized access to higher-level security mechanisms. Additionally, this layered approach allows efficient key updates and re-authentication processes while minimizing key exposure, thus enhancing the overall security of 5G communications. With the use of advanced key derivation functions (KDFs), secure key separation, and context-based key generation, 5G provides a more resilient and robust security framework compared to previous generations of mobile networks. Key Management OverviewIn the 5G security architecture, key management is a carefully orchestrated process distributed across different network functions. The core of this system involves a clear division of responsibility between the radio and core networks. The Access and Mobility Management Function (AMF), a core network entity, directly manages the Non-Access Stratum (NAS) security keys, which protect the signaling link between the user's device and the core. While the gNB is responsible for deriving the Access Stratum (AS) keys to secure the radio interface, it cannot do so independently. This process is initiated by the AMF, which provides the gNB with a crucial base key, KgNB. This entire key hierarchy originates during the primary authentication procedure, where functions like the Authentication Server Function (AUSF) and the Security Anchor Function (SEAF) generate the initial high-level keys that the AMF subsequently uses to secure the connection.
Roles of Network Entities in Key ManagementIn 5G networks, the management of security keys is a detailed and hierarchical process, with distinct roles assigned to each network function to ensure a robust, end-to-end security framework. This process begins with the AUSF handling the primary authentication procedure, which generates an intermediate key that is passed to the SEAF. Acting as the security anchor, the SEAF uses this to derive the anchor key, K_SEAF, which is then provided to the AMF. The AMF holds a central role, managing all NAS security by deriving integrity and encryption keys from K_AMF and also kickstarting AS security. It does this by deriving the crucial base key, KgNB, and forwarding it along with the UE's security capabilities to the gNB. Finally, the gNB takes on the responsibility for the radio interface, using the received KgNB to derive a full suite of keys for RRC and user plane protection, and then activating this security with the UE. This clear separation of duties, from the long-term key storage in the UDM to the final key derivation in the gNB, ensures a secure and coordinated activation of both NAS and AS protection. AMF (Access and Mobility Management Function):
AUSF (Authentication Server Function):
SEAF (Security Anchor Function):
UDM (Unified Data Management) / ARPF (Authentication Credential Repository and Processing Function):
gNB (Next Generation NodeB):Responsible for AS security key derivation:
Overview of Key Derivation FlowIn 5G, the security key derivation follows a distinct hierarchical flow, cascading from the core network down to the radio equipment. The process begins during primary authentication, where a long-term secret key, K, stored in the UDM, is used by the AUSF and SEAF to generate an anchor key, K_SEAF. This key is then passed to the AMF, which derives its own master key, K_AMF. From this single point, the AMF orchestrates two parallel security activations: it derives the NAS integrity and encryption keys to secure signaling with the core network, and it derives the base key for the radio, K_gNB. Finally, the AMF provides this K_gNB to the gNB, which then uses it to derive all the necessary AS keys for protecting traffic over the radio interface, completing the chain of trust from the core to the airwaves.
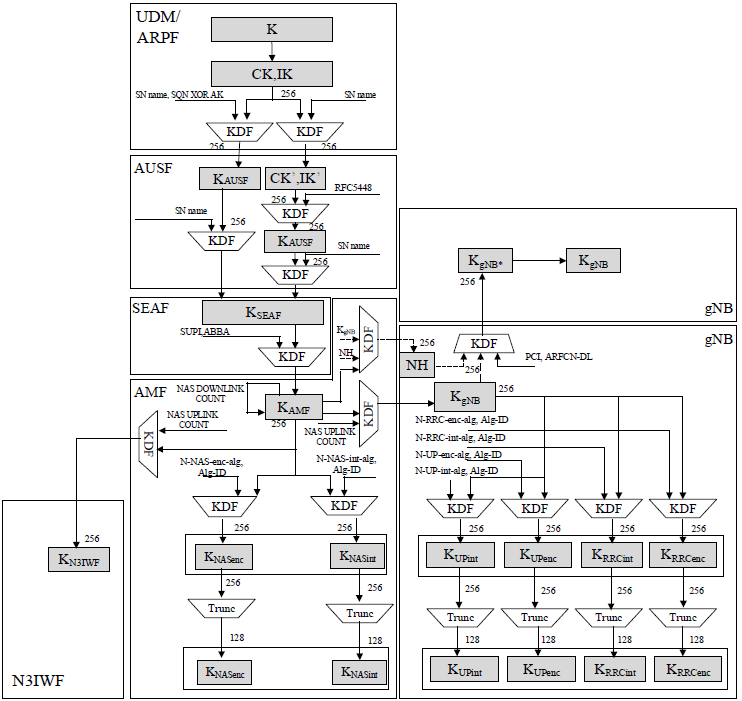
Key hierarchy generationThe 5G key hierarchy is more granular than 4G’s, with separate keys for NAS, RRC, and user plane security, as well as for 3GPP and non-3GPP access. This improves security by limiting the impact of a compromised key. The inclusion of K_AUSF and K_SEAF provides better key separation between the home and serving networks, enhancing security in roaming scenarios. The support for both 5G-AKA and EAP-AKA' ensures flexibility for different authentication methods, while the derivation of user plane keys (K_UPint, K_UPenc) adds an extra layer of security for data traffic, which was optional in 4G. Overall, this hierarchy ensures robust, layered security for 5G communications. < 33.501 - Figure 6.2.1-1: Key hierarchy generation in 5GS >
The diagram is divided into two sides: the Network side (HPLMN and Serving Network) and the UE side, showing how keys are derived and shared between entities like the UDM/ARPF, AUSF, SEAF, AMF, N3IWF, and the UE (via USIM and ME, Mobile Equipment). The process starts with a root key and progresses through multiple derivations to create keys for specific purposes, ensuring key separation and security.
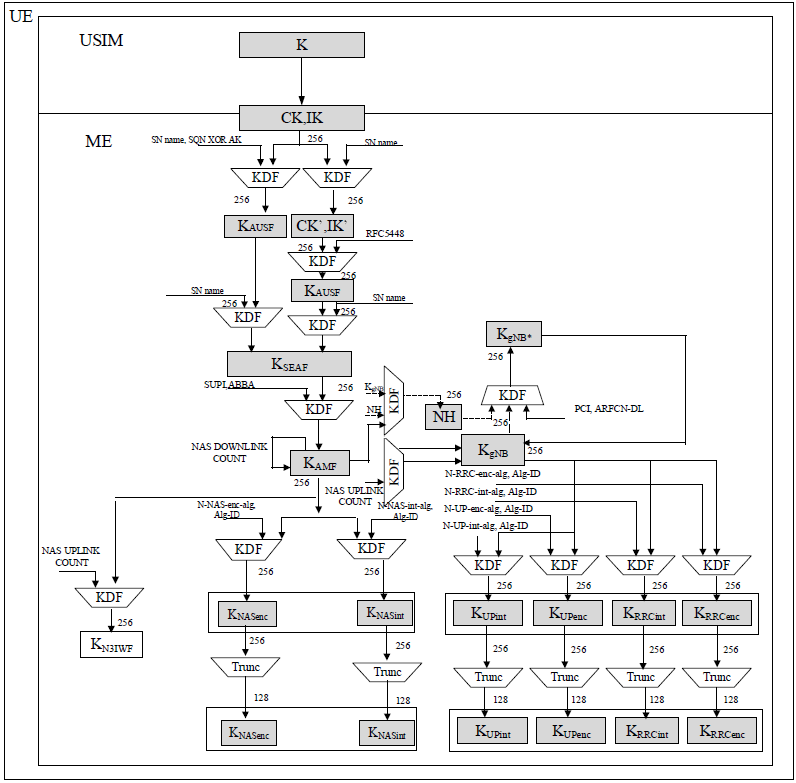
Key distribution and key derivation scheme for 5G for network nodesKey derivation and key distribution are fundamental security mechanisms used in communication systems like 5G to ensure secure authentication, encryption, and data integrity. Key derivation is the process of generating cryptographic keys from an initial secret, often referred to as a master key or root key. Instead of using a single key for all security functions, the system derives multiple keys for different purposes, such as authentication, encryption, and integrity protection. This hierarchical approach enhances security by limiting the exposure of the master key while ensuring that different parts of the network use separate keys for specific tasks. Key distribution refers to the secure transfer and management of these derived keys across various network nodes and entities. In a system like 5G, once the keys are derived at the authentication center (UDM/ARPF), they are securely distributed to relevant components such as AUSF, SEAF, AMF, and gNB. Each entity receives only the necessary keys required for its specific role. For example, the serving network (SEAF) gets the anchor key, while the access network (gNB) receives encryption and integrity protection keys. Together, key derivation and distribution ensure that sensitive information remains protected throughout the communication process. By implementing a structured hierarchy of keys, security is maintained even if one key is compromised, as it does not expose higher-level or unrelated security credentials. The diagram shown below illustrates the key distribution and derivation scheme in 5G. It depicts how cryptographic keys are generated and securely distributed among different network entities to ensure authentication, encryption, and integrity protection. At the highest level, the UDM/ARPF (Unified Data Management / Authentication Credential Repository and Processing Function) holds the primary key K, which is used to derive authentication vectors. Using a key derivation function (KDF), it generates CK, IK (Cipher Key and Integrity Key) and further derives the KAUSF key, which is transferred to the AUSF (Authentication Server Function). The AUSF processes this key and passes it down to the SEAF (Security Anchor Function) after further derivation. The SEAF then derives the KSEAF key, which is the main security anchor at the serving network. From this, the AMF (Access and Mobility Management Function) generates KAMF, which forms the basis for various security functions such as NAS encryption and integrity protection. The AMF derives KNASenc and KNASint, which are responsible for securing NAS layer communication between the UE and the core network. For radio link security, the gNB (next-generation NodeB) derives KgNB, used for securing RRC and UP transmissions. From KgNB, additional keys are derived for RRC integrity protection (KRRCint), RRC encryption (KRRCenc), UP encryption (KUPenc), and UP integrity protection (KUPint). For non-3GPP interworking, a separate key KN3IWF is generated, ensuring secure integration with untrusted non-3GPP access networks. Overall, the 5G security framework introduces hierarchical key derivation, improving security by ensuring that different network functions operate with their own specialized keys while maintaining a strong authentication chain from the UDM/ARPF down to the gNB. < 33.501 - Figure 6.2.2-1: Key distribution and key derivation scheme for 5G for network nodes >
Key distribution and key derivation scheme for 5G for the UEThe diagram shown below illustrates the key distribution and key derivation scheme for 5G within UE,. It details how cryptographic keys are derived and securely distributed within the UE to ensure authentication, encryption, and integrity protection. At the core of the system, the USIM (Universal Subscriber Identity Module) holds the primary K key, which serves as the root of the security framework. The Mobile Equipment (ME) utilizes this key to generate CK (Cipher Key) and IK (Integrity Key) via a Key Derivation Function (KDF). These keys are then used to derive additional keys required for different security processes. The next step involves the generation of KAUSF, which is used for authentication with the Authentication Server Function (AUSF) in the core network. After authentication, the system derives KSEAF, which serves as the anchor key for further security mechanisms in the Serving Network (SEAF). Once the UE establishes communication, KAMF is derived from KSEAF and is responsible for securing NAS (Non-Access Stratum) messages. It further derives KNASenc for NAS encryption and KNASint for NAS integrity protection, ensuring secure exchanges between the UE and the core network. For radio link security, KgNB is derived, which serves as the main key for access network protection. From KgNB, additional keys are derived for different security purposes:
For non-3GPP interworking, a separate key KN3IWF is derived to secure communication over non-trusted access networks. The hierarchical key derivation structure ensures that each layer of security is built upon a previous level, minimizing key exposure and enhancing overall security. If a lower-level key is compromised, the root key K remains protected, maintaining the integrity of the authentication and encryption processes. < 33.501 - Figure 6.2.2-2: Key distribution and key derivation scheme for 5G for the UE >
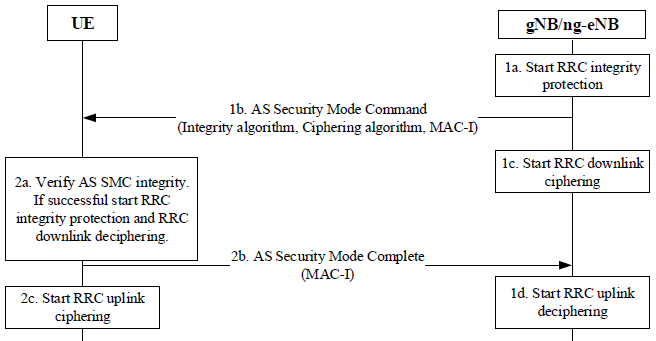
AS Security Mode CommandThe AS (Access Stratum) Security Mode Command in 5G is a critical procedure that ensures secure communication between the UE and the gNB (next-generation NodeB) by activating encryption and integrity protection for both signaling and user data. This procedure is initiated by the gNB after the successful establishment of a secure connection and is used to negotiate and apply security algorithms for RRC (Radio Resource Control) and UP (User Plane) traffic. The Security Mode Command message sent by the gNB includes the selected encryption and integrity protection algorithms, which the UE must acknowledge and confirm before security settings take effect. The process also prevents security breaches by ensuring that all messages exchanged between the UE and the network are protected against eavesdropping and tampering. By implementing robust cryptographic protections and ensuring mutual agreement on security parameters, the AS Security Mode Command plays a crucial role in maintaining the confidentiality, integrity, and reliability of 5G network communications. The following diagram illustrates the AS (Access Stratum) Security Mode Command procedure in 5G networks, detailing the steps to establish security between the User Equipment (UE) and the gNB/ng-eNB (5G base station). The process ensures that RRC (Radio Resource Control) signaling and user plane data are protected through integrity and ciphering mechanisms. < 33.501 - Figure 6.7.4-1: AS Security Mode Command Procedure >
Below is an explanation of the steps involved:
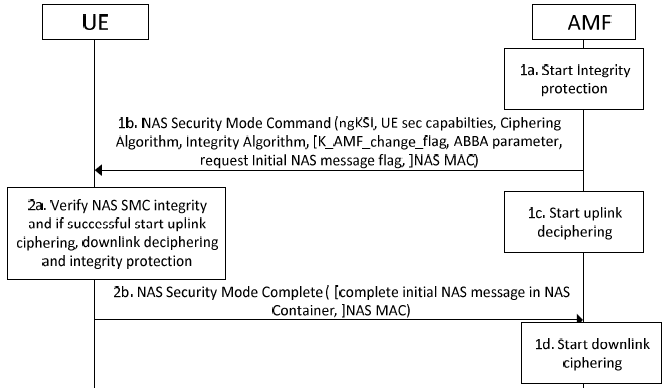
NAS Security Mode CommandThe NAS (Non-Access Stratum) Security Mode Command in 5G is a vital procedure that establishes encryption and integrity protection for NAS signaling between the UE and the Access and Mobility Management Function (AMF). This procedure is initiated by the AMF after a successful authentication process to enforce security policies and protect signaling messages from eavesdropping and tampering. The Security Mode Command message sent by the AMF specifies the encryption and integrity algorithms to be used, ensuring that the UE and the core network agree on a common security configuration. Upon receiving this command, the UE verifies and responds with a Security Mode Complete message, confirming the applied security settings. This mechanism is crucial in safeguarding NAS messages that handle mobility, session management, and authentication processes, thereby enhancing the confidentiality, integrity, and resilience of 5G communications. The following diagram illustrates the NAS (Non-Access Stratum) Security Mode Command procedure in 5G networks, detailing the steps to establish security between the UE and the Access and Mobility Management Function (AMF). This process ensures that NAS signaling messages between the UE and the core network are protected through integrity and ciphering mechanisms < 33.501 - Figure 6.7.2-1: NAS Security Mode Command procedure >
Below is an explanation of the steps involved:
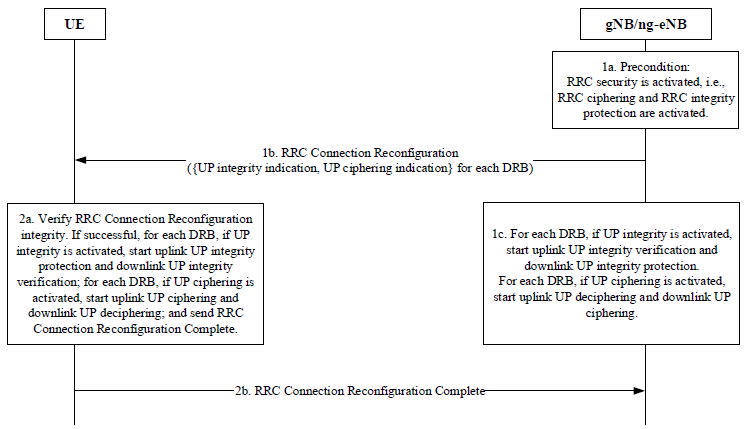
User Plane SecurityUser Plane Security in 5G is a critical mechanism that ensures the confidentiality, integrity, and protection of user data transmitted between the User Equipment (UE) and the network. It is established after successful authentication and security mode procedures, where the gNB and UE derive encryption and integrity protection keys from the key hierarchy. Encryption is applied to safeguard user data against eavesdropping, while integrity protection ensures that transmitted packets remain unaltered and authentic. The security configuration, including the selected encryption and integrity algorithms, is determined during the Access Stratum (AS) Security Mode Command procedure. By implementing strong cryptographic protections, user plane security in 5G enhances privacy, prevents unauthorized access, and ensures the reliability of data transmission across the network. Follwoing diagram illustrates the User Plane (UP) security activation mechanism in 5G networks, detailing the process to enable integrity and ciphering protection for user data between the User Equipment (UE) and the gNB/ng-eNB (5G base station). The procedure builds on the already established RRC (Radio Resource Control) security to activate UP security for each Data Radio Bearer (DRB). < 33.501 - Figure 6.6.2-1: User plane (UP) security activation mechanism >
Below is an explanation of the steps involved:
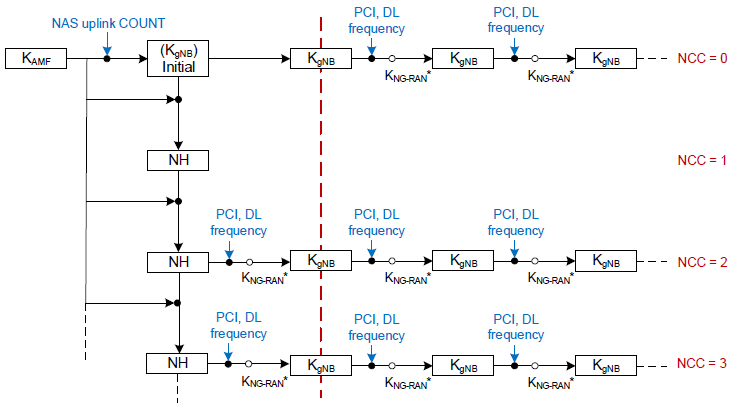
Key Handling in HandoverKey handling in handover in 5G is a crucial security process that ensures the continuity and protection of encrypted communications as the UE moves between different gNBs. During handover, the security context, including encryption and integrity keys, must be securely transferred while preventing key reuse and exposure. The key derivation follows a hierarchical structure, where a new key, KgNB, is generated for the target gNB based on the previously established security anchor key. This ensures forward and backward security, preventing attackers from deriving past or future keys even if a session key is compromised. The handover key management process also incorporates the Next Hop (NH) mechanism, which strengthens security by generating fresh keys for each handover event. By maintaining a robust key handling framework, 5G ensures seamless, secure transitions between cells, reducing the risk of interception and ensuring uninterrupted, protected communication. Following diagram illustrates the model for key handling during handovers in 5G networks, focusing on the key chaining process to maintain security as the User Equipment (UE) transitions between gNBs (5G base stations). The process ensures continuity of secure communication by deriving and distributing new keys while managing the NAS (Non-Access Stratum) uplink COUNT and Next Hop (NH) parameters. < 33.501 - Figure 6.9.2.1.1-1: Model for the handover key chaining >
Below is an explanation of the key handling and chaining process:
Reference :
|
||