|
IP/Network |
|||||||||||
|
Encryption
In a formal and dry definition, encryption is a mechanism to secure Confidentiality of data. In a casual term, it is a method of converting the original data (usually readable/understandable by human or a tool) into a garbage-like (not real garbage :) data so that nobody or no tool can understand as it is.
Encryption Algorithms
Followings are some of common Encryption algorithms that were / are used. (Some of the algorithm are not often used now since they can be broken easily, but I think those old algorithm would still be very important in terms of understanding the fundamental mechanism of Encryption algorithm)
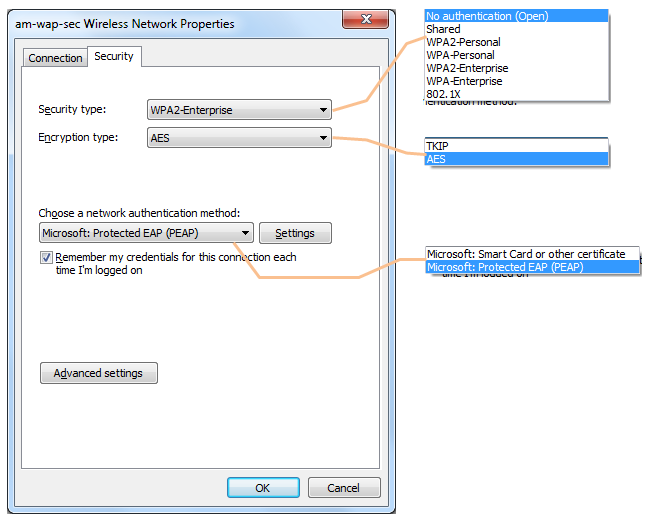
You may think none of these seems related to your daily use of your tools (like PC or SmartPhone etc). But if you open up your WiFi settings, you can easily find some of these algorithm is really being used in your PC or SmartPhone. Of course, you may not know exactly what's going on inside and you don't need to know.
I want to show you the details of the simplest encryption algorithm which is not used any more but would be very helpful for you to understand the general concept of Encryption algorithm. The algorithm I want to see in details is RC4.
This algorithm goes through following steps. i) Chose 'Secret Key' ii) Initialize S[] vector iii) Perform KSA(Key Scheduling Algorithm) : Main function of this step is to shuffle the elements in S[] vector iv) Perform PRGA(Pseudo-Random Generator Algorithm) : Main function of this step is to generate a 'keystream'. v) As a result of PRGA, a keystream is generated, vi) the keystream from step iv) is used to encrypt the data. This encryption is done by (data XOR keystream)
If you have just a little bit of experence of C code, following code would be a better explanation for the algorithm. int _tmain(int argc, _TCHAR* argv[]) { int i,j=0,x,t; unsigned char S[256]; unsigned char out[1024]; unsigned char stream[1024]; int key_len,out_len,idx;
// Step 1 : Specify any key you want to use. unsigned char key[]={"Key"};
// Step 2 : Initialize S[] vector. for (i=0; i < 256; ++i) S[i] = i;
// Step 3 : Perform KSA(Key Scheduling Algorithm) key_len = 3; for (i=0; i < 256; ++i) { j = (j + S[i] + key[i % key_len]) % 256; // Following three line is just for swapping S[i] and S[j] t = S[i]; S[i] = S[j]; S[j] = t; };
// Step 4 : Perform PRGA(Pseudo-Random Generator Algorithm) out_len = 9; j = 0; for (x=0; x < out_len; ++x) { i = (i + 1) % 256; j = (j + S[i]) % 256; // Following three line is just for swapping S[i] and S[j] t = S[i]; S[i] = S[j]; S[j] = t; // this is the out keystream of PRGA and will be used to encrypt the user data. out[x] = S[(S[i] + S[j]) % 256]; };
for (idx=0; idx < out_len; idx++) printf("%02X ",out[idx]); return 0; }
// once you have the output keystream (out[]) and user data (userdata[]), you can encrypt it // by following simple operation (this is the psudo code, not C code. so don't copy and try this line.
// encrypted_data = out XOR user_data
Mode of Operation
Block Cipher (e.g, DES or AES) defines on how to apply the ciphering algorithm to a certain fixed length called 'block'. Since the length of the block is not so large, single block cipher usually used for a short data. When the data length is long, we need to combine or apply Block Cipher repeatedly. Mode of Operation defines how to combine multiple block cipher or how to repeadly apply the block cipher to cipher long data.
There are several types of mode of operation as listed below.
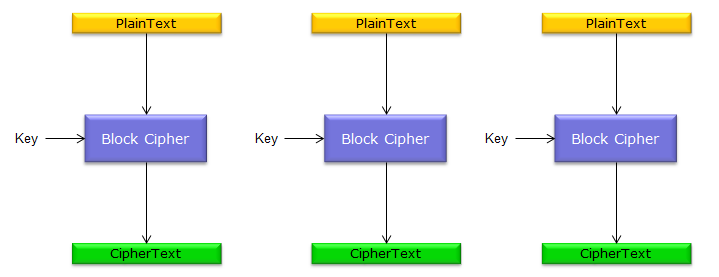
< ECB >
ECB stands for Electronic Code Book. As you see in the following illustration, ECB uses multiple Block Ciphers just aligned in parallel and no interaction among those blocks. So it would be easy to implement but can be easily broken into. Personally I haven't seen any case where ECB is used. Probably nobody would use this for now (Jun 2015).
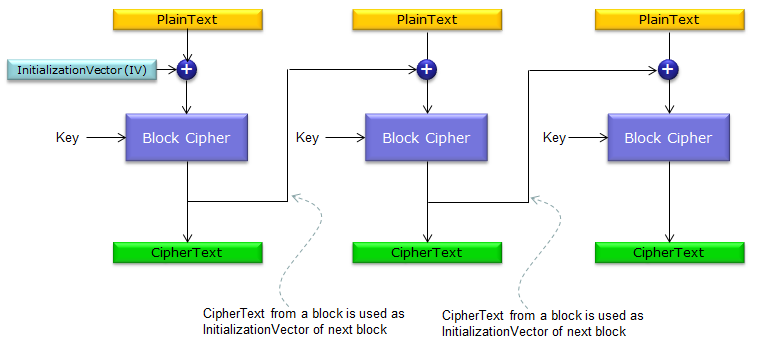
< CBC >
CBC stands for Cipher Block Chaining. As the name implies, multiple Block Coders are chained as shown below. As you see here, each block cloder takes not only Ciphering Key but also Initialization Vector (IV) as parameters. The IV only for the first block is predefined one and the ciphered text the first block is used as IV for the second block and the ciphered text the second block is used as IV for the third block and so on.
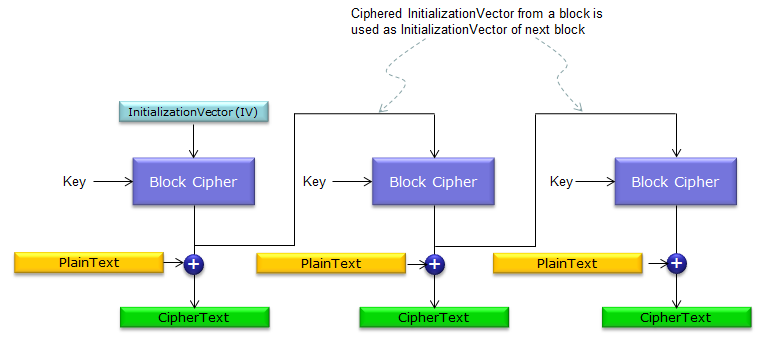
< OFB >
OFB stands for Output Feed Back. Overall concept is similar to CBC meaning multiple blocks are chained together. In this case, the block cipher ciphers only IV using the ciphering Key and the output of the block cipher is XORed to PlainText (Input Data) that creates the final CipherText. In this method, the IV only for the first block is predefined one and the output of the first Block cipher is used as IV for the second block and the output of the second Block cipher is used as IV for the third block and so on.
|
|||||||||||