|
IP/Network |
||
|
D-H(Diffie–Hellman) Key Exchange
If you are unfamiliar with the concept of Key Exchange or want to get basic understandings on why we need a special key exchange technique, I strongly recommend watching this public lecture video : Royal Institution Christmas Lectures 2008 - Lecture 4 - Untangling the Web
If you are still interested in the topic and want to know some mathematical background behind it. This page would give you some insight on it. This page is based on Wikipedia : Diffie–Hellman key exchange. I tried to convert the Wikipedia page into a couple of diagrams and some comments in my own words.
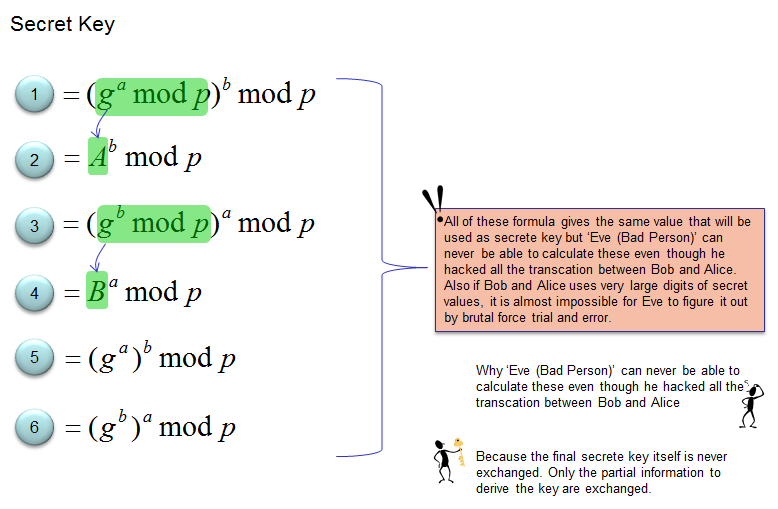
The main idea behind this algorithm is as follows. Mathematically there are many different ways that produces the same number which will be used as Secret key. This is based on a specific branch of mathematics called Modular Math. This is why you may heard so frequently about the term 'Modular Math' when you see/watch things about D-H algorithm (or most of other key generation/exchange algorithm). How do you know that all of these formular produce the same value ? It is the job of Mathematician :) Any way, the idea is that the party A (let's call this Alice) and party B (let's call this Bob) never exchange the secret key itself, they just exchange a partial informations in a special way that Alice and Bob can calculate the secret key with the partial information that they received and an additional information that they have but never exchanged 'directly', but the bad person (let's call this Eve) can never get enough information that can produce the same secret key. I think I need to add a couple of more comments to make this more accurate, but if I try to explain more it would confuse you more. I would recommend you to see the video linked at the beginning of this page (more specifically the parts they change information with colored liquid) and then get back to this math part and protocol sequence part.)
NOTE : In real use case, the parameter g,p,A,B are shared (exchanged) between the two parties (e.g, Bob and Alice) and known to hacker (e.g, Eve) as well. But a is known only to Bob (Bob selected this value) and b is known only to Alice (Alice selected this number). It is designed that Eve (the hacker) can never catch the parameter a, b. The (5) and (6) is the private key caluclated by Alice and Bob respectively. As you see in the equation, whatever value is used for a and b, the value (5) and (6) are same. It means that whatever value a and b are selected, Bob and Alice can derive the same value (same private key)
Now let's think of the famous situation as shown below. Alice and Bob is communicating each other and the bad person Alice is trying to steal the information.
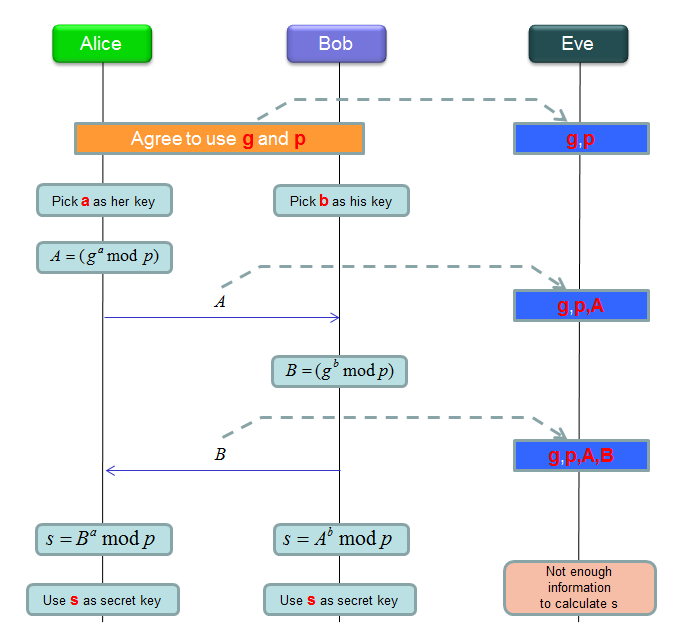
Now let me illustrate what's happening on the side of Alice, Bob and Eve. And what kind of information is exchanged between Alice and Bob, what kind of of information can be stolen by Eve.
NOTE : In order to figure out the secrete key 's', the parameter 'a' and 'b' should be known. But Eve can never know these parameter because those parameters are never exchanged between Alice and Bob and Even couldn't get it by eavesdropping. NOTE : The point in this process is that Bob and Elice does not change the key(symmetric key) directly. They just exchange some paramters and intermediate calculation result to derive the same key value on both side. But one those informations being exchanged are not enough to generate the key. Therefore, even though Eve (eavesdropper) hijack all the information being exchanged between Alice and Bob, she (Eve) cannot derive the key.
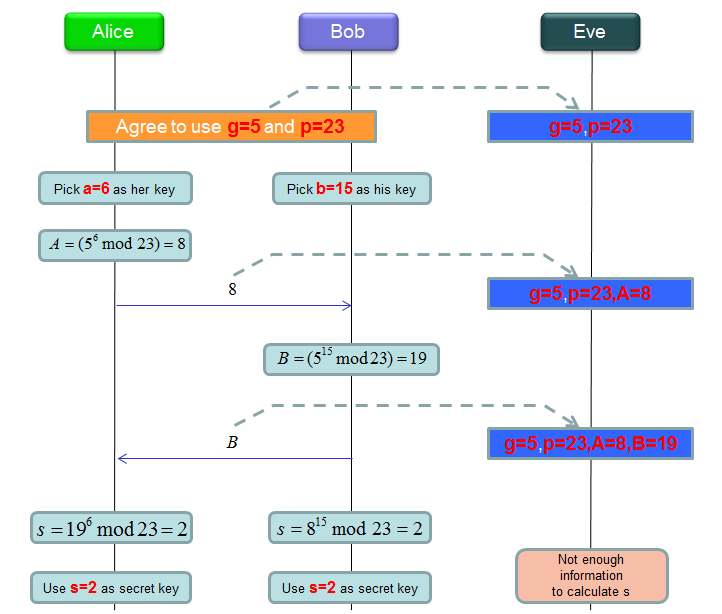
Following is the same as the illustration as above.. the only difference is that I put a specific numbers to give you more concrete understanding. The numbers and the calculation result came from WiKipedia and I just expressed in the form of sequence diagram.
|
||