|
|
||
|
NAS Integrity is a mechanism that can let you (UE or Network) know if a NAS message is modified or corrupted in some way (See Confidentiality and Integrity pagefor the details of the concept of Integrity). The NAS Integrity Algorithm is a vital mechanism within LTE networks designed to ensure the integrity of NAS messages exchanged between the UE and the network. This mechanism enables both the UE and the network to detect if a NAS message has been tampered with, modified, or corrupted during transmission. By implementing integrity protection, the NAS Integrity Algorithm provides a cryptographic safeguard that verifies the authenticity and reliability of signaling messages. Through the use of cryptographic algorithms such as EIA (EPS Integrity Algorithms), the system computes a Message Authentication Code (MAC) that is appended to the message before it is transmitted. When the message is received, the MAC is recalculated and compared to ensure the message has not been altered. This process not only protects the communication from malicious attacks but also ensures the system's robustness and security, playing a critical role in maintaining trust and reliability in LTE communications.
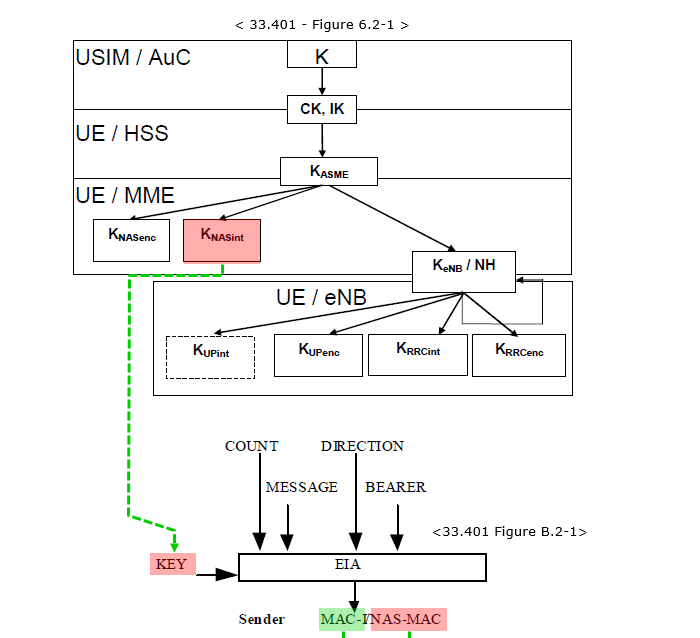
Overall Key FlowsOverall flow from Key Generations and final output for NAS Integrity can be illustrated as follows : The key points of this diagrams are
Followings are breakdown of the illustration and brief descriptions of each step. Key Derivation Process:
eNB (eNodeB) Key Derivation:
Integrity Protection:K_NASint is specifically used in this diagram to protect the integrity of NAS signaling messages. A cryptographic algorithm (EIA - EPS Integrity Algorithm) ensures that the NAS message is not tampered with during transmission by calculating a Message Authentication Code (MAC).
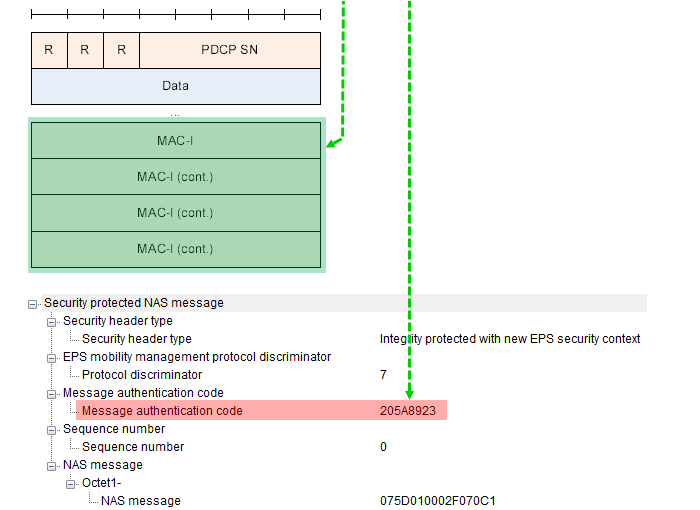
What does NAS Integrity Algorithm do ?Simply put, NAS Integrity (in LTE and UMTS) is to calculate the Message Authentication Code (MAC, shown in Red) using various inputs (shown in Blue and Green) and to calculate MAC-I field in PDCP PDU as illustrated below.
The NAS Integrity Algorithm ensures the integrity of NAS (Non-Access Stratum) messages by:
Followings are breakdown of the diagram above
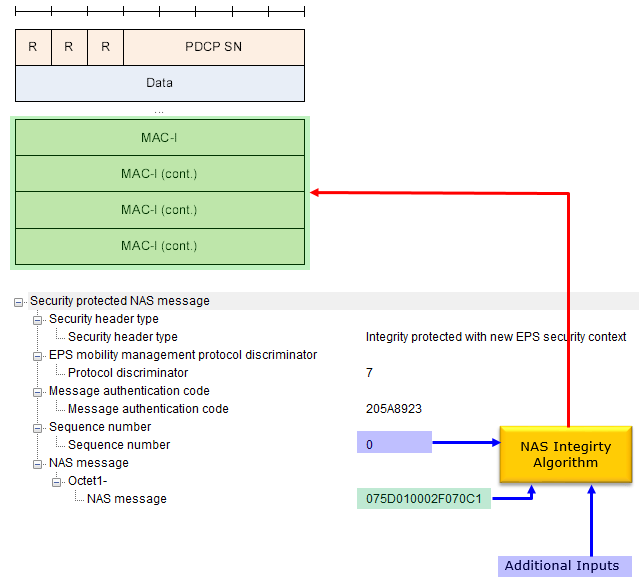
How MAC is integrated into PDCP ?The PDCP PDU (Protocol Data Unit) is a key component in LTE communication, responsible for carrying data such as NAS messages, user data, or control plane signaling, and it includes the PDCP Sequence Number (PDCP SN) to maintain order and synchronization. Integrity protection in the PDCP PDU ensures that the transmitted data remains authentic and free from tampering. This is achieved through the use of a cryptographic code known as MAC-I (Message Authentication Code - Integrity), which is calculated using the NAS Integrity Algorithm. MAC-I serves as a safeguard to verify the integrity of the PDCP PDU, ensuring that it has not been altered during transmission. Once computed, the MAC-I is appended to the PDCP PDU, allowing the receiver to validate the authenticity of the message upon reception.
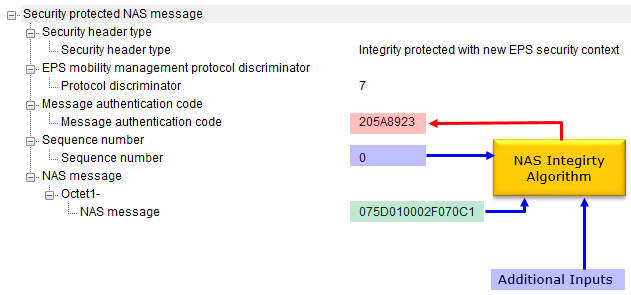
This is breakdown of the diagram shown above :
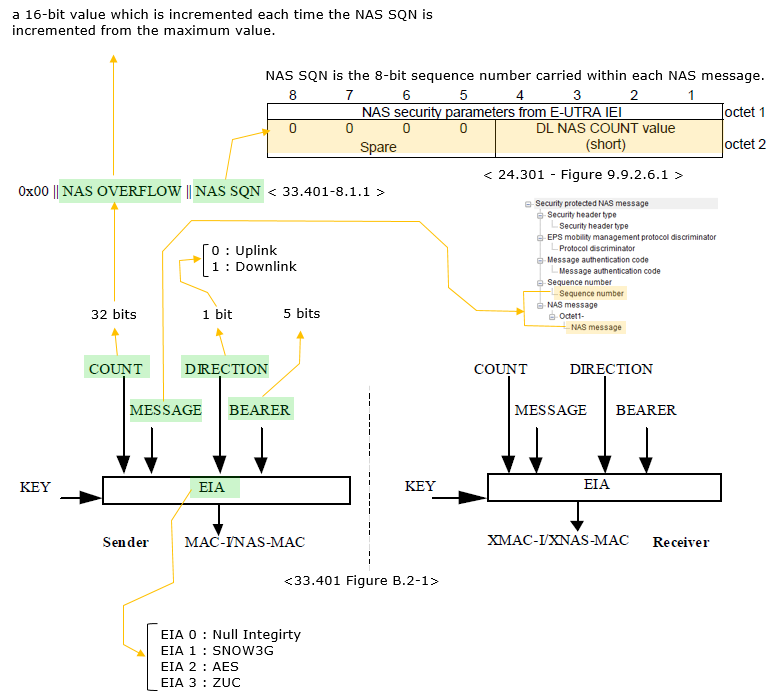
Key Generation DetailsThe NAS Integrity Algorithm used in LTE is called EIA(EPS Integrity Algorithm). High level functionality of EIA can be illustrated as below. This section explains the key generation process for the NAS Integrity Algorithm (EIA) used in LTE, highlighting how integrity protection for NAS messages is achieved. It provides a detailed view of how the required inputs, such as the sequence number, direction, bearer, and message, contribute to generating the Message Authentication Code (MAC). It highlights the systematic approach to generating and verifying message integrity in LTE using the NAS Integrity Algorithm. By utilizing the COUNT, Direction, Bearer, and Message as inputs, along with a cryptographic key, the system ensures that messages are secure and have not been tampered with during transmission. This process is vital for maintaining the integrity and security of NAS signaling in LTE networks.
As shown above, there are several different EIA that can be used for LTE and you need to go through a lot of other documents to understand the details of these algorithm. For EIA1 as an example, refer to SNOW3G page. Key Components in the Process
EIA (EPS Integrity Algorithm)
Reference :
|
||