|
IPsec-AH
AH stands for 'Authentication Header'. It is a component of IPSec protocol that can provide source authentication and data integrity. However, AH does not perform any data encription. AH (Authentication Header) is a protocol used in IPSec to provide authentication and integrity protection for IP packets.
AH provides a strong level of authentication and integrity protection for IP packets, helping to prevent various types of attacks, such as packet sniffing, tampering, and replay attacks. However, it does not provide confidentiality protection, so it is often used in combination with ESP, which provides encryption as well as authentication and integrity protection.
Two Types of AH : Transport Mode and Tunnel Mode
AH can be used in either transport mode or tunnel mode.
- In transport mode, the AH header is inserted between the IP header and the transport-layer header (e.g. TCP, UDP), providing protection only for the transport-layer protocol.
- In tunnel mode, the entire original IP packet is encapsulated inside a new IP packet, with the AH header inserted between the new IP header and the original IP header, providing protection for the entire IP packet.
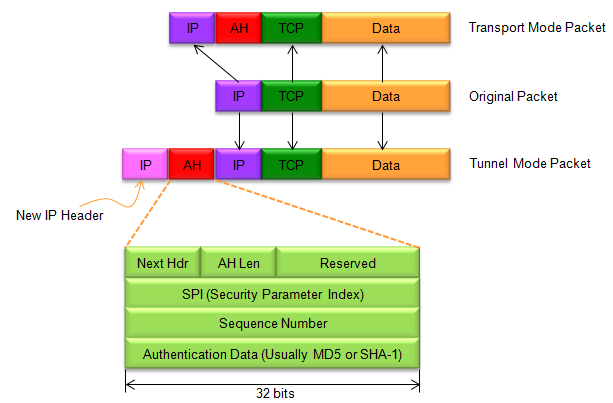
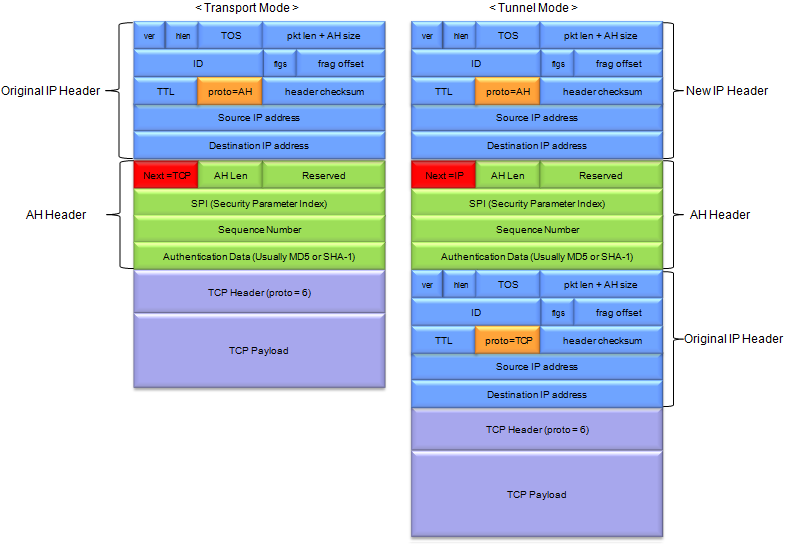
Followings are descriptions of each field in AH Header :
- Next Header: This field identifies the protocol (e.g. TCP, UDP) that follows the AH header in the packet.
- AH Len: This field specifies the length of the AH header and the payload that it protects.
- Reserved: This field is reserved for future use and must be set to zero.
- Security Parameters Index (SPI): This identifies the security association (SA) used to protect the packet.
- Sequence Number: This field is used to prevent replay attacks by providing a unique identifier for each packet.
- Authentication Data: This variable-length field contains the message authentication code (MAC) used to authenticate the packet. The length of this field depends on the authentication algorithm used.
|
|

