|
|
|||||||||||||||||||||||||||||||
|
rAPP stands for RAN Application. These are applications that run on the Non-Real-Time RAN Intelligent Controller (Non-RT RIC). rApps are software applications designed to run on the Non-Real-Time RAN Intelligent Controller (Non-RT RIC). Their primary purpose is to realize various RAN management and optimization use cases in an automated way, with control loops operating on a time scale of one second and longer
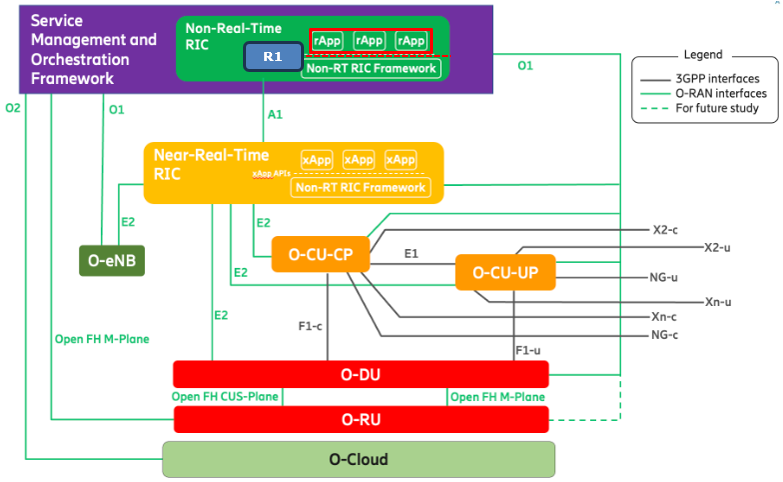
rAPP in ORAN ArchitectureIn ORAN architecture, rAPPs (RAN Intelligent Controller applications) are software programs that run on the Non-Real Time RIC (Non-RT RIC). This Non-RT RIC is a key component in the O-RAN architecture responsible for handling network management and optimization tasks that don't require immediate, real-time responses. rAPPs runs on the Non-RT RIC and communicating via the R1 interface and enable intelligent, policy-driven control and optimization of the RAN on a timescale suitable for non-real-time operations. The R1 interface plays a crucial role here as it serves as the communication pathway between the rAPPs and the underlying Non-RT RIC framework. It enables rAPPs to access necessary data, interact with other components, and ultimately contribute to the overall service management and orchestration of the network.
Key Features of rAPPsrAPPs are characterized by several key features that enable them to perform their role effectively within the O-RAN architecture. It is designed to be data driven and highly flexible and adaptable. Followings are a list of Key Features of rAPP
Common Use Cases of rAPPsrAPPs represent a cornerstone of intelligent network management within the O-RAN architecture. Operating on the Non-Real Time RIC, rAPPs are specifically designed to handle tasks that don't demand immediate, real-time responses. Leveraging their capabilities in data analysis, policy implementation, and automation, rAPPs empower network operators to optimize network performance, enhance energy efficiency, and enable a multitude of innovative use cases, contributing significantly to the evolution of 5G and beyond networks. Followings are some of common use cases of rAPPs Traffic SteeringrAPPs can analyze network traffic patterns, congestion levels, and user demands in a non-real-time manner to make intelligent decisions on how to route traffic. This may involve dynamically adjusting routing paths, load balancing across different cells, or even steering users to different frequency bands or network slices based on their service requirements. By doing so, rAPPs can enhance network performance, reduce congestion, and ensure an optimal quality of experience for users. Energy SavingsrAPPs can play a crucial role in energy-saving initiatives within the RAN. They can analyze historical data, traffic patterns, and cell load over longer durations to identify opportunities to put certain network elements into sleep modes or adjust their power levels during periods of low utilization. They can also implement intelligent energy-saving policies based on user behavior and network conditions, contributing to a greener and more sustainable network. Anomaly DetectionrAPPs can leverage their access to historical data and machine learning capabilities to identify abnormal patterns or behaviors within the network. This may include detecting sudden spikes in traffic, unusual signaling patterns, or performance degradations that could indicate potential issues or security threats. By detecting these anomalies early on, rAPPs can trigger timely actions, such as alarms, diagnostics, or even automated mitigation steps, to prevent service disruptions and ensure network reliability. Long-term Load BalancingWhile short-term load balancing is often handled by near-real-time RIC components, rAPPs can excel at long-term load balancing strategies. They can analyze historical load patterns, user mobility trends, and even predictable events (e.g., sports games) to make proactive decisions on resource allocation and cell configuration to avoid congestion and ensure optimal capacity utilization over longer durations. Mobility OptimizationrAPPs can enhance user mobility experiences by analyzing mobility patterns and predicting user movements. This can enable them to make proactive handover decisions, pre-allocate resources in anticipated target cells, and optimize mobility parameters to minimize service disruptions during handovers. This can lead to smoother handovers, reduced call drops, and improved quality of service for mobile users. Network Planning and DeploymentrAPPs can contribute to network planning and deployment processes by providing insights derived from long-term data analysis and network performance monitoring. They can help identify coverage gaps, capacity bottlenecks, and potential areas for optimization or expansion. This information can be invaluable for network operators in making informed decisions regarding network upgrades, new cell deployments, or capacity enhancements. Intelligent AutomationrAPPs can automate various network management and optimization tasks, reducing the need for manual intervention and streamlining operations. They can implement intelligent policies, trigger automated responses to network events, and even provide recommendations to network operators based on data-driven insights. This automation can lead to improved operational efficiency, reduced costs, and faster response times to network issues. R1 : Interface between rAPP and Non-Near RT RICThe R1 interface is a standardized and consistent communication channel between the Non-RT RIC and the rAPPs. It abstracts the complexity of the underlying network while providing a set of services and data that the rAPPs can leverage to enhance RAN performance, support automated network management, and execute non-real-time control functions. RESTful R1 Service APIsAs many of other application level interfaces, R1 is also based on RESTful mechanism. They enable a variety of essential functions, categorized into the following service domains: Service Management and Exposure ServicesService Management and Exposure Services(SME) form a crucial foundation within the O-RAN architecture. They facilitate the dynamic interplay between service providers (rApps) and the Non-RT RIC platform, ensuring efficient service registration, discovery, and real-time updates on service availability.
Data Management and Exposure ServicesData Management and Exposure Services(DME) play a pivotal role in the O-RAN ecosystem by facilitating the seamless handling of data within the network. It encompasses a suite of APIs designed to streamline the processes of data registration, discovery, and access, ensuring that the right data gets to the right place at the right time.
RAN Operations, Administration, and Maintenance (OAM) Related ServicesRAN Operations, Administration, and Maintenance (OAM) Related Services are a collection of APIs (Application Programming Interfaces) that enable the management and upkeep of the Radio Access Network (RAN) within the O-RAN architecture. These services are essential for ensuring the smooth operation, efficient configuration, and timely troubleshooting of the RAN, which is the fundamental infrastructure responsible for connecting user devices to the core network.
A1 Related ServicesA1 Related Services specifically address the management and orchestration of A1 policies. These policies are instrumental in governing the dynamic interactions and behaviors between the Non-RT RIC and the near-RT RIC . By providing a structured framework for policy creation, modification, and enforcement, A1 Related Services enable intelligent and adaptive control of the RAN, facilitating efficient resource allocation, optimized performance, and support for a wide array of 5G use cases.
Type of Supported ServicesIn today’s world of advanced and open radio networks, the R1 interface is a key enabler of smooth communication between applications (rApps) and the management systems that oversee the network. It serves as the connection point that allows rApps to interact with the Service Management and Orchestration (SMO) framework, providing essential services to ensure the network runs efficiently. The R1 interface supports a range of functions, from managing and sharing data to monitoring and optimizing the Radio Access Network (RAN). It also connects with the A1 interface to manage policies and use network insights for smarter decisions. By providing a common platform for these services, the R1 interface makes it easier to integrate solutions from different vendors, helping operators build flexible and intelligent networks. This allows network managers to improve performance, troubleshoot issues faster, and make better use of network resources, paving the way for more robust and future-ready mobile networks. There are various services supported over R1 interface that can be summarized as below. Service Management and Exposure ServicesThe Register Service API is a crucial operation in the O-RAN architecture, enabling a Service Producer (e.g., an API Consumer) to register services with the API Producer. The operation ensures the service is defined, authorized, and made discoverable for subsequent interactions. The Register Service API uses an HTTP POST request to facilitate the registration of a service. The API Consumer submits the necessary details about the service to the API Producer, which processes the request and generates the required resources for the service. Key Steps in the Operation Step 1: POST Request from API Consumer
Step 2: Validation by API Producer
Step 3: Resource Creation and Response
Example Request (API Consumer → API Producer) POST /<apiFld>/service-apis Content-Type: application/json { "rAppId": "rApp12345", "serviceName": "AnalyticsService", "version": "1.0", "capabilities": ["data-processing", "trend-analysis"], "endpoint": "http://analytics.example.com/api" } Response (API Producer → API Consumer) HTTP/1.1 201 Created Content-Type: application/json Location: http://example.com/service-apis/analytics-service-12345
{ "serviceId": "analytics-service-12345", "serviceName": "AnalyticsService", "status": "Registered", "capabilities": ["data-processing", "trend-analysis"], "endpoint": "http://analytics.example.com/api" } The Service Discovery API allows API Consumers (e.g., rApps) to perform service discovery operations, enabling them to identify and interact with services published by API Producers. This API is critical for discovering available services based on specific parameters like service name, version, or capabilities. The Query Service APIs operation is based on an HTTP GET request. The API Consumer queries the API Producer to retrieve a list of all services the consumer is authorized to access. The API Producer processes the query, applies filtering criteria, and returns relevant service profiles. Key Steps in the Operation Step 1: GET Request from API Consumer
Step 2: Validation by API Producer
Step 3: Response from API Producer
API Prototype GET /<apiRoot>/service-apis/v1/allserviceapis Headers: Authorization: Bearer <token> Query Parameters: api-name=<ServiceName> api-version=<ServiceVersion> api-invoker-id=<InvokerId> Response: 200 OK [ { "serviceId": "<ServiceId>", "name": "<ServiceName>", "version": "<ServiceVersion>", "capabilities": ["<Capability1>", "<Capability2>"], "endpoint": "<ServiceEndpoint>" } ] Example Request (API Consumer → API Producer) GET /apiRoot/service-apis/v1/allserviceapis?api-name=AnalyticsService&api-version=1.0 Headers: Authorization: Bearer abcd1234 Response (API Producer → API Consumer) HTTP/1.1 200 OK Content-Type: application/json [ { "serviceId": "12345", "name": "AnalyticsService", "version": "1.0", "capabilities": ["data-processing", "trend-analysis"], "endpoint": "http://analytics.example.com/api" }, { "serviceId": "67890", "name": "OptimizationService", "version": "2.0", "capabilities": ["resource-allocation", "traffic-analysis"], "endpoint": "http://optimization.example.com/api" } ] Service events subscriptionThis API allows the API Consumer to subscribe to and unsubscribe from service event notifications The Subscribe Service Events API allows an API Consumer (e.g., an rApp) to subscribe to service event notifications provided by the API Producer. This ensures the API Consumer can be notified of specific events, such as new services being registered or changes in existing services. The Subscribe Service Events operation uses an HTTP POST request where:
Key Steps in the Operation Step 1: POST Request from API Consumer
Step 2: Validation by API Producer
Step 3: Response from API Producer
API Prototype POST /{subscriberId}/subscriptions Headers: Content-Type: application/json Authorization: Bearer <token> Body: { "eventTypes": ["<EventType1>", "<EventType2>"], "callbackUrl": "<CallbackURL>" } Response: 201 Created Headers: Location: /{subscriberId}/subscriptions/{subscriptionId} Body: { "subscriptionId": "<SubscriptionId>", "status": "Subscribed" } Example Request (API Consumer → API Producer) POST /rApp12345/subscriptions Headers: Content-Type: application/json Authorization: Bearer abcd1234 Body: { "eventTypes": ["ServiceRegistration", "ServiceUpdate"], "callbackUrl": "http://example.com/notifications" } Response (API Producer → API Consumer) HTTP/1.1 201 Created Headers: Location: /rApp12345/subscriptions/sub-67890 Body: { "subscriptionId": "sub-67890", "status": "Subscribed" } The Unsubscribe Service Events API allows an API Consumer (e.g., an rApp) to remove an existing subscription for service event notifications. This operation ensures that the API Consumer stops receiving notifications for a previously subscribed event. The Unsubscribe Service Events operation is performed using an HTTP DELETE request where:
Key Steps in the Operation Step 1: DELETE Request from API Consumer
Step 2: Validation by API Producer
Step 3: Response from API Producer
API Prototype DELETE /{subscriberId}/subscriptions/{subscriptionId} Headers: Authorization: Bearer <token> Response: 204 No Content Example Request (API Consumer → API Producer) DELETE /rApp12345/subscriptions/sub-67890 Headers: Authorization: Bearer abcd1234 Response (API Producer → API Consumer) HTTP/1.1 204 No Content
The Notification Service API is used by the API Producer to send event notifications to all subscribed API Consumers. This operation ensures that API Consumers are informed about relevant events (e.g., service registration, updates, or deletion) in real-time, based on their subscriptions. The operation is based on an HTTP POST request:
Key Steps in the Operation Step 1: Notification Trigger
Step 2: HTTP POST Request to Callback URI
Step 3: Handling by API Consumer
API Prototype POST {callbackURI} Headers: Content-Type: application/json Body: { "eventType": "<EventType>", "eventTimestamp": "<ISO8601 Timestamp>", "eventDetails": { "serviceId": "<ServiceId>", "serviceName": "<ServiceName>", "serviceVersion": "<ServiceVersion>", "additionalInfo": "<Details>" } } Response: 200 OK Example Request (API Producer → API Consumer) POST http://example.com/notifications Headers: Content-Type: application/json Body: { "eventType": "ServiceRegistration", "eventTimestamp": "2024-12-04T12:00:00Z", "eventDetails": { "serviceId": "12345", "serviceName": "AnalyticsService", "serviceVersion": "1.0", "additionalInfo": "New service registered." } } Response (API Consumer → API Producer) HTTP/1.1 200 OK Input and Output of rAPPThe fundamental role of an rAPP is to adjust the configuration of the Radio Access Network (RAN) in response to decisions derived from a variety of inputs collected directly from the RAN itself. In practice, this process typically involves the rAPP receiving Performance Management (PM) data-such as traffic statistics, network load metrics, signal quality indicators, and other operational insights-from the RAN. Leveraging this information, the rAPP then makes informed decisions and outputs Configuration Management (CM) data, which may involve adjusting parameters like transmit power levels, antenna tilt angles, or handover thresholds. In other words, the rAPP constantly refines and optimizes the RAN’s configuration by analyzing performance-related inputs and implementing corresponding configuration changes, ultimately striving to enhance network efficiency, reliability, and overall service quality Followings are some examples of PM data (Input) : These are just examples and the detailed list of data would vary depending on network infra vendor.
Followings are some examples of CM data (output) : These are also just possible examples and the detailed list of data would vary depending on network infra vendor.
Typical Approaches to rAPP ImplementationWhen integrating rAPPs (RAN applications) into the network ecosystem, two predominant strategies often emerge: rule-based configurations and AI/ML-driven intelligence. Each approach has distinct advantages, considerations, and applicable scenarios, and the selection between them typically depends on factors such as network complexity, performance objectives, and the availability of high-quality data. Rule-Based ApproachA rule-based approach involves codifying network logic and decision criteria into a set of predefined parameters and directives. These rules are usually derived from deep domain expertise, standardized guidelines, and well-understood operational principles. For instance, a rule might dictate that if the cell load exceeds a certain threshold, the rAPP should reduce transmit power or initiate handovers to neighboring cells to balance traffic. The simplicity of this method can be appealing, as it offers transparency, easier debugging, and straightforward traceability. Network operators can clearly identify the conditions that trigger an action, making the system more predictable and manageable. However, rule-based methods may struggle to scale when networks become highly dynamic, diverse, and complex, as manually crafting and updating rules for every possible scenario can be both time-consuming and prone to human error.
AI/ML-Based ApproachBy contrast, an AI/ML-based approach leverages advanced models and algorithms—such as reinforcement learning, supervised learning, or unsupervised clustering—to inform rAPP decisions. Instead of relying solely on fixed rules, these models learn patterns directly from historical and real-time Performance Management (PM) data. For example, a machine learning model might predict the optimal configuration parameter by correlating current traffic conditions, interference patterns, user distribution, and past outcomes. Over time, these algorithms continually refine their decision-making strategies as more data becomes available, allowing them to adapt to emerging network conditions without explicit human intervention. This can lead to more efficient network optimization, faster response to changes, and improved scalability. However, the effectiveness of AI/ML models heavily depends on the quality and quantity of training data, the clarity of reward signals (in the case of reinforcement learning), and the complexity of the model itself. Additionally, ensuring explainability and maintaining trust in AI-driven decisions can be challenging.
Balancing the Two ApproachesIn practice, network operators often employ a hybrid strategy. For areas of the network where conditions are stable and well-understood, rule-based logic can provide a reliable baseline. Meanwhile, AI/ML models can be introduced in more dynamic scenarios or complex domains, where patterns are less obvious and benefits from automated, data-driven optimization are clearer. Over time, as the sophistication and confidence in AI/ML solutions grow, the system can gradually shift toward more advanced, adaptive models that continuously enhance overall network performance and resilience.
Typical AI/ML Models for rAPPThese rAPPs leverage a variety of machine learning (ML) models tailored to specific use cases in the Radio Access Network (RAN). Below, we explore the common ML model types, their general descriptions, typical use cases, and the associated pros and cons. Followings are summary of various ML models that would be used for each use cases and their pros and cons.
Supervised Learning ModelsSupervised learning models use labeled datasets where the desired output is known. These models learn to map input features to target outputs, making them ideal for predictive tasks. They are particularly effective when historical data is available to train the models.
Unsupervised Learning ModelsUnsupervised learning models deal with unlabeled datasets, discovering hidden structures and patterns. These models are used for clustering, dimensionality reduction, and anomaly detection, making them suitable for exploratory tasks in network optimization.
Reinforcement Learning (RL)Reinforcement learning (RL) is an advanced ML approach where an agent learns by interacting with an environment and receiving feedback through rewards. This approach is well-suited for dynamic, decision-making problems in network optimization.
Time-Series ModelsTime-series models analyze sequential data to identify trends and patterns over time. They are essential for predictive tasks involving temporal dependencies, such as traffic forecasting and fault prediction.
Graph-Based ModelsGraph-based models operate on graph structures, where data points (nodes) are connected by relationships (edges). These models are excellent for scenarios involving network topology, user relationships, and interference patterns.
Reference
|
|||||||||||||||||||||||||||||||