|
IP/Network |
||||||||||||||||||||||
|
TCP
TCP stands for Transmission Control Protocol. This may be one of the most common protocols in relation to any IP network. For example, most of the application layer protocol we are commonly using these days , like HTTP, HTTPS, SMTP, POP3, IMAP, SSH, FTP, Telnet ect, are typically encapsulated in TCP packet.
TCP is a kind of session protocol which requires a special procedure to establish the connnection between the client and server and also requires a special procedure to release the connection between them.
To begin the communication using TCP, the client and server has to go through a special sequence to establish the connection and this sequence goes as shown below. It is done by 3 steps. That's why this procedure is often called 3 way handshaking or 3 way negotiation.
Step (1) : Client send a TCP SYN Packet to server to request connection establishment. At this step, the client assign a specific sequence number (this is called as ISN) as the initial (first) sequence number. This is not zero, it is the number generated by a special algorithm in such a way that it cannot easily been guessed by any intruder. As you see in the following example, the real initial sequence number is randomly (specially) assigned as in (C), but in wireshark it is labeled to be 0 as shown in (A). Also, this initial packet has SYN flag is set to be '1'.
Transmission Control Protocol, Src Port: 42206 (42206), Dst Port: sip (5060), Seq: 0, Len: 0 Source port: 42206 (42206) Destination port: sip (5060) [Stream index: 0] Sequence number: 0 (relative sequence number) <=== (A) Header length: 40 bytes Flags: 0x002 (SYN) 000. .... .... = Reserved: Not set ...0 .... .... = Nonce: Not set .... 0... .... = Congestion Window Reduced (CWR): Not set .... .0.. .... = ECN-Echo: Not set .... ..0. .... = Urgent: Not set .... ...0 .... = Acknowledgment: Not set .... .... 0... = Push: Not set .... .... .0.. = Reset: Not set .... .... ..1. = Syn: Set <=== (B) [Expert Info (Chat/Sequence): Connection establish request (SYN): server port sip] [Message: Connection establish request (SYN): server port sip] [Severity level: Chat] [Group: Sequence] .... .... ...0 = Fin: Not set Window size value: 65535 [Calculated window size: 65535] Checksum: 0x9d0f [validation disabled] [Good Checksum: False] [Bad Checksum: False] Options: (20 bytes), Maximum segment size, SACK permitted, Timestamps, No-Operation (NOP), Window scale Maximum segment size: 1440 bytes Kind: MSS size (2) Length: 4 MSS Value: 1440 TCP SACK Permitted Option: True Kind: SACK Permission (4) Length: 2 Timestamps: TSval 4294945900, TSecr 0 Kind: Timestamp (8) Length: 10 Timestamp value: 4294945900 Timestamp echo reply: 0 No-Operation (NOP) Type: 1 0... .... = Copy on fragmentation: No .00. .... = Class: Control (0) ...0 0001 = Number: No-Operation (NOP) (1) Window scale: 6 (multiply by 64) Kind: Window Scale (3) Length: 3 Shift count: 6 [Multiplier: 64]
0000 00 30 64 0b 6c 69 00 00 91 05 fa 92 86 dd 60 00 .0d.li........`. 0010 00 00 00 28 06 40 20 01 00 00 00 00 00 02 00 00 ...(.@ ......... 0020 00 00 00 00 00 01 20 01 00 00 00 00 00 02 00 00 ...... ......... 0030 00 00 00 00 00 02 a4 de 13 c4 0c f3 f8 fa <== (C) ................ 0040 00 00 a0 02 ff ff 9d 0f 00 00 02 04 05 a0 04 02 ................ 0050 08 0a ff ff ac 6c 00 00 00 00 01 03 03 06 .....l........
Step (2) : Server accept the SYN request and send ACK and SYN in a single packet to the Client. At this step, the Server assign a specific sequence number (this is called as ISN) as the initial (first) sequence number. This is not zero, it is the number generated by a special algorithm in such a way that it cannot easily been guessed by any intruder. As you see in the following example, the real initial sequence number is randomly (specially) assigned as in (E), but in wireshark it is labeled to be 0 as shown in (A).
Transmission Control Protocol, Src Port: sip (5060), Dst Port: 42206 (42206), Seq: 0, Ack: 1,Len: 0 Source port: sip (5060) Destination port: 42206 (42206) [Stream index: 0] Sequence number: 0 (relative sequence number) <== (A) Acknowledgment number: 1 (relative ack number) <== (B) Header length: 40 bytes Flags: 0x012 (SYN, ACK) 000. .... .... = Reserved: Not set ...0 .... .... = Nonce: Not set .... 0... .... = Congestion Window Reduced (CWR): Not set .... .0.. .... = ECN-Echo: Not set .... ..0. .... = Urgent: Not set .... ...1 .... = Acknowledgment: Set <== (C) .... .... 0... = Push: Not set .... .... .0.. = Reset: Not set .... .... ..1. = Syn: Set <== (D) [Expert Info (Chat/Sequence): Connection establish acknowledge (SYN+ACK): server port sip] [Message: Connection establish acknowledge (SYN+ACK): server port sip] [Severity level: Chat] [Group: Sequence] .... .... ...0 = Fin: Not set Window size value: 8192 [Calculated window size: 8192] Checksum: 0x4037 [validation disabled] [Good Checksum: False] [Bad Checksum: False] Options: (20 bytes), Maximum segment size, No-Operation (NOP), Window scale, SACK permitted, Timestamps Maximum segment size: 1440 bytes Kind: MSS size (2) Length: 4 MSS Value: 1440 No-Operation (NOP) Type: 1 0... .... = Copy on fragmentation: No .00. .... = Class: Control (0) ...0 0001 = Number: No-Operation (NOP) (1) Window scale: 8 (multiply by 256) Kind: Window Scale (3) Length: 3 Shift count: 8 [Multiplier: 256] TCP SACK Permitted Option: True Kind: SACK Permission (4) Length: 2 Timestamps: TSval 73513, TSecr 4294945900 Kind: Timestamp (8) Length: 10 Timestamp value: 73513 Timestamp echo reply: 4294945900 [SEQ/ACK analysis] [This is an ACK to the segment in frame: 119] [The RTT to ACK the segment was: 0.000129000 seconds]
0000 00 00 91 05 fa 92 00 30 64 0b 6c 69 86 dd 60 00 .......0d.li..`. 0010 00 00 00 28 06 80 20 01 00 00 00 00 00 02 00 00 ...(.. ......... 0020 00 00 00 00 00 02 20 01 00 00 00 00 00 02 00 00 ...... ......... 0030 00 00 00 00 00 01 13 c4 a4 de 18 c3 b3 cb <==(E) 0c f3 ................ 0040 f8 fb <== (F) a0 12 20 00 40 37 00 00 02 04 05 a0 01 03 .... .@7........ 0050 03 08 04 02 08 0a 00 01 1f 29 ff ff ac 6c .........)...l
Step (3) : Now the client send ACK to the Server for the SYN packet. You see here both Sequence Number and Acknowledgement number got incremented by 1.
Transmission Control Protocol, Src Port: 42206 (42206), Dst Port: sip (5060), Seq: 1, Ack: 1, Len: 0 Source port: 42206 (42206) Destination port: sip (5060) [Stream index: 0] Sequence number: 1 (relative sequence number) <== (A) Acknowledgment number: 1 (relative ack number) <== (B) Header length: 32 bytes Flags: 0x010 (ACK) 000. .... .... = Reserved: Not set ...0 .... .... = Nonce: Not set .... 0... .... = Congestion Window Reduced (CWR): Not set .... .0.. .... = ECN-Echo: Not set .... ..0. .... = Urgent: Not set .... ...1 .... = Acknowledgment: Set <== (C) .... .... 0... = Push: Not set .... .... .0.. = Reset: Not set .... .... ..0. = Syn: Not set .... .... ...0 = Fin: Not set Window size value: 1350 [Calculated window size: 86400] [Window size scaling factor: 64] Checksum: 0xdab5 [validation disabled] [Good Checksum: False] [Bad Checksum: False] Options: (12 bytes), No-Operation (NOP), No-Operation (NOP), Timestamps No-Operation (NOP) Type: 1 0... .... = Copy on fragmentation: No .00. .... = Class: Control (0) ...0 0001 = Number: No-Operation (NOP) (1) No-Operation (NOP) Type: 1 0... .... = Copy on fragmentation: No .00. .... = Class: Control (0) ...0 0001 = Number: No-Operation (NOP) (1) Timestamps: TSval 4294945901, TSecr 73513 Kind: Timestamp (8) Length: 10 Timestamp value: 4294945901 Timestamp echo reply: 73513 [SEQ/ACK analysis] [This is an ACK to the segment in frame: 120] [The RTT to ACK the segment was: 0.016912000 seconds]
0000 00 30 64 0b 6c 69 00 00 91 05 fa 92 86 dd 60 00 .0d.li........`. 0010 00 00 00 20 06 40 20 01 00 00 00 00 00 02 00 00 ... .@ ......... 0020 00 00 00 00 00 01 20 01 00 00 00 00 00 02 00 00 ...... ......... 0030 00 00 00 00 00 02 a4 de 13 c4 0c f3 f8 fb <== (D) 18 c3 ................ 0040 b3 cc <== (E) 80 10 05 46 da b5 00 00 01 01 08 0a ff ff .....F.......... 0050 ac 6d 00 01 1f 29 .m...)
The type and the property of a TCP packet is determined by various flags located in the TCP header. Some of the important flags are listed below.
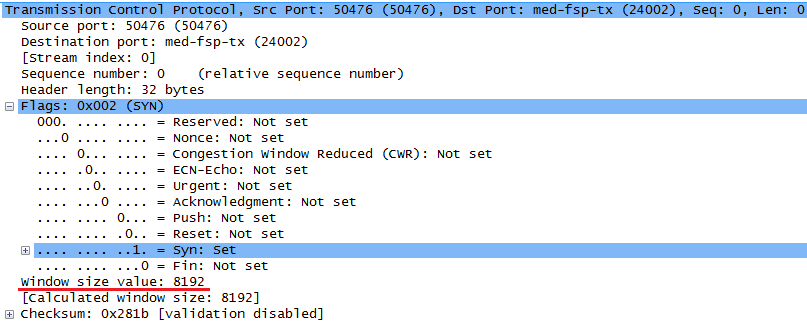
In TCP header, there is a important field named as Window Size as shown below.
What does this mean ? It indicate the amount of space (in byte) left in the receiving buffer. Basically it notifies the other party "I have this much of space in my receiving buffer, so you can send that amout of data to me at maximum". In other words, "Don't send me the data more than that". What if this window size is set to be 0 ? What does it mean ? It means "I have no space to receive any further data. So don't send me any data to me now".
As you may guess, this window size would be very important indicator for traffic flow control.. so is used as very important indicator for troubleshooting various TCP related issues.
There are various ways to change this window size adaptively and followings are some of the web posts that may be helpful for you.
TCP Window Size is represented by a 16 bit number. It means that the maximum window size that can be represented is 64 K. What if we need to represent a window size larger than 64 K ? It cannot be reprented by the 16 bit number. To overcome this restriction, they come out with an option field called 'Window Scale'. If 'Window Scale' field is set, the real window size is calculated by as follows.
Real Window Size (Calculated Window Size) = Window Size Value x 2^(Window Scale in bits)
Window Scale can be set independantly for Client and Server. Window Scale for Client can be set by SYN packet as shown below.
Window Scale for Server can be set by SYN,ACK packet as shown below.
MSS represent the maximum size of a TCP packet. This size can be configured differently on Client and Server and the size information is exchanged by [SYN] and [SYN,ACK] packet as shown below. One thumb rule to set the MSS is to set it to be (MTU - 40) bytes. MTU is a kind of maximum packet size for each network card. So if you set MSS too large and the whole IP packet gets larger than MTU, it should be fragmented into multiple packets to make it fit to physical packet limitation and it may influence negatively on TCP throughput.
Just for your reference, you can figure out MTU of each of your network card by using following command if you are using Windows.
File : Network_IP_TCP_Example01
Packet (1) ---------------------------------------------------------------------------------------------
Packet (2) ---------------------------------------------------------------------------------------------
Packet (3) ---------------------------------------------------------------------------------------------
Packet (4) ---------------------------------------------------------------------------------------------
Packet (5) ---------------------------------------------------------------------------------------------
Packet (6) ---------------------------------------------------------------------------------------------
Packet (14) ---------------------------------------------------------------------------------------------
Packet (15) ---------------------------------------------------------------------------------------------
Packet (16) ---------------------------------------------------------------------------------------------
Packet (17) ---------------------------------------------------------------------------------------------
[1] Understanding Asymmetric Links, Bu ers and Bi-Directional TCP Performance [2] TCP SEQUENCE & ACKNOWLEDGEMENT NUMBERS - SECTION 2
|
||||||||||||||||||||||