|
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
SecurityWLAN Security is a special mechanism which allows only a specific person (machine) to get access to a specific WLAN Network. In more formal term, it is a mechanism to assure confidentiality and integrity of data flowing over WLAN network. Since this can easily be very dry topic and I don't have expert level knowledge of these algorithm, I want to try to describe this in more practical and intuitive level.
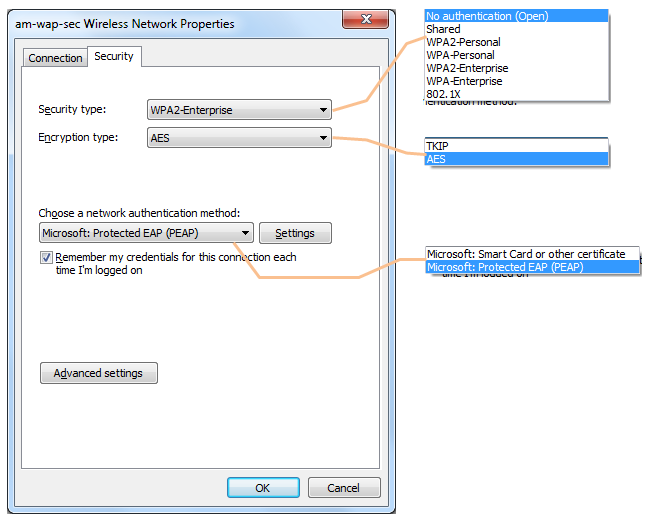
Before you jump into a bunch of boring documents about Security, I would recommend to get familiar with some terminologies you would come across in technical documents. One good way to get familiar with would be to have some time to take a little bit closer look at some tools that almost everybody have used at some point but never paid closer attention. First example is from WLAN setting on my own PC on the network that I am allowed to use. My WLAN interface has following types of Security options. You may see different options on your PC and your WLAN network. Don't try to understand everything in details here. Just get familiar with some terms of WPA, WPA2 or AES etc.
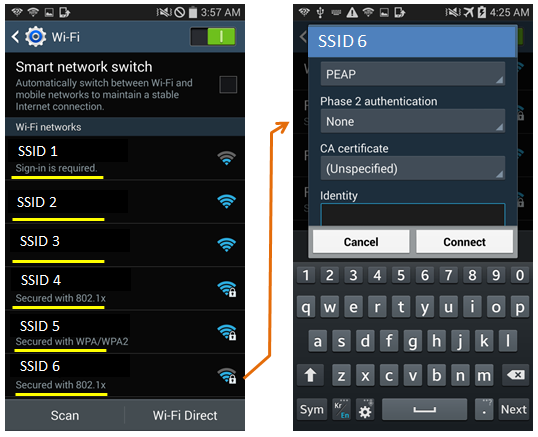
Here goes another example. Following is from one of WiFi options shown on my mobile phone. You would also see a lot of new terminologies here. Again, just try to get familiar with the terms ..
Now you would be wondering exactly where and how these algorithms play roles during WiFi attach or Data communication process. For this, I would recommend you to go through WiFi Protocol page and overall understanding of WiFi Protocol. And then take closer look at step 4, 5, 8, 9, 10, 11 of Sample log of WiFi Aattach process. (The detailed procedure and parameters in each step would vary depending on each algorithm but you would get a big picture from the page). Now with a little bit of familiarity with basic keywords and overall understanding on protocol, let's take a small step into some of commonly used security algorithm. You can get a pretty good tutorial of overall concept of WLAN Security from the list of Video Tutorial at the bottom of the page. WLAN Security TypesWLAN security is an essential aspect of wireless networking, as it helps protect your network from unauthorized access and keeps your data safe. Over the years, several security protocols have been developed for WLANs, each with different levels of protection. Here are the main WLAN security types < WEP >WEP was the first security protocol introduced for Wi-Fi networks. It uses the RC4 stream cipher for encryption and supports 64-bit and 128-bit encryption keys. However, WEP has significant security vulnerabilities and is considered outdated and insecure. It's not recommended for use in modern WLANs. WEP stands for Wired Equivalent Privacy and it has following properties/functionalities.
Drawback of WEP : Since there is no key management and uses shared key, every wireless station and AP has the same "preshared" key that is used during authentication and encryption. It means you have to manually distribute the key to every device and every AP and it would be very cumbersome to change key because once you change it and you have to redistribute them all manually. So usually every device will use the same/static key for a long time giving more chance for hackers to break the system. < WPA >WPA stands for WiFi Protected Access. It is proposed as Interim solution that offers key management using the 802.1X authentication framework and performs improved encryption and integrity checking. WPA was introduced as an interim solution to address WEP's security weaknesses. It uses Temporal Key Integrity Protocol (TKIP) for encryption, which is an improvement over WEP, and also incorporates Message Integrity Check (MIC) to protect against data tampering. However, WPA still uses the RC4 stream cipher, which has known vulnerabilities, making it less secure than more recent security protocols. It has following properties/functionalities.
< WPA2 >This is a kind of WPA evolution and is specified in IEEE 802.16i. In most part, it is same as WPA but it uses improved encryption mechanism called AES. WPA2 is a more secure and widely used security protocol for WLANs. It replaces TKIP with the more robust Advanced Encryption Standard (AES) cipher for encryption, providing a higher level of security. WPA2 supports two authentication methods: WPA2-Personal (also known as WPA2-PSK) for home and small office networks, which uses a pre-shared key, and WPA2-Enterprise for larger networks, which relies on a RADIUS server for authentication. < WPA 3 >WPA3 is the latest security protocol and provides several enhancements over WPA2. It offers stronger encryption through the Simultaneous Authentication of Equals (SAE) method, which replaces the pre-shared key in WPA2-Personal with a more secure key exchange. WPA3-Enterprise provides an even higher level of security with 192-bit encryption. WPA3 also improves security for public Wi-Fi networks with Opportunistic Wireless Encryption (OWE). WLAN Authentication TypesWLAN authentication is the process of verifying the identity of devices trying to connect to a wireless network. Authentication helps to prevent unauthorized access and protect your network from potential threats. There are many different types of WLAN Authentication methods and the list gets longer and longer. Followings are some of the common methods and I will keep update as I learn more.
Open system authenticationOpen System Authentication doesn't require any authentication or credentials to connect to the Wi-Fi network. Devices can connect without providing any identification, making it the least secure authentication method. Open networks are typically found in public places like coffee shops, libraries, or airports, where the priority is easy access rather than security. In reality 'Open System Authentication' means 'No Authentication'. You would ask 'Is there anybody who really use this ?'. The answer is Yes, largely for two reason. One is just using an Access Point for special testing purpose and in other more common situation is where you don't do any Authentication on AP (Access Point) level so you would set 'Open' in AP Security, but you let the packet goes through additional security system sitting behind AP. You would see this kind of methods being used in many company.
Status Code carries various information defined in 802.11 and it includes the status of whether attach is successful or not. Refer to 802.11 Association Status, 802.11 Deauth Reason codes for the details of the code. Shared Key AuthenticationShared Key Authentication is an older method that uses a pre-shared key (PSK) known to both the client and the access point. The client and access point exchange encrypted messages to authenticate each other. However, Shared Key Authentication is considered insecure due to its reliance on the flawed WEP security protocol and is not recommended for use.
WPA-Personal / WPA2-Personal / WPA3-Personal (Pre-shared Key)WPA-Personal, WPA2-Personal, and WPA3-Personal use a pre-shared key (PSK) for authentication. All devices connecting to the network need to provide the correct PSK to gain access. This method is straightforward to set up and is suitable for home and small office networks. The security of the PSK method depends on the strength of the password and the encryption protocol used (WPA, WPA2, or WPA3).
WPA-Enterprise / WPA2-Enterprise / WPA3-Enterprise (802.1X Authentication)WPA-Enterprise, WPA2-Enterprise, and WPA3-Enterprise use the 802.1X authentication framework, which provides a more robust and scalable authentication solution for larger networks. It relies on a RADIUS server or another authentication server to manage user credentials and access policies. This method allows for individual user authentication, making it suitable for corporate or enterprise networks that require a higher level of security and access control.
Captive PortalA Captive Portal is an authentication method often used in public Wi-Fi networks, like hotels or cafes, where users need to provide additional information or agree to terms and conditions before accessing the network. When connecting to a captive portal, users are redirected to a web page where they need to enter their credentials, such as a username and password, or provide other details like an email addres
Authentication using SSID of AP
MAC address filtering
WPA in Authentication and SecurityYou would notice WPA family is used both in Authentication process and Security Process. Any major differences between the two ? WPA authentication is about verifying the identity of devices trying to connect to a Wi-Fi network, while WPA security algorithms focus on the encryption methods used to protect data transmitted over the network. WPA Authentication:WPA authentication refers to the process of verifying the identity of a device when it tries to connect to a Wi-Fi network. WPA authentication can be either "WPA-Personal" (also known as WPA-PSK) or "WPA-Enterprise" (also known as WPA-802.1X). WPA-Personal uses a pre-shared key (PSK) for authentication, which is a passphrase known to both the device and the access point. WPA-Enterprise uses an authentication server, such as a RADIUS server, to authenticate users based on their individual credentials, like usernames and passwords or digital certificates. WPA Security Algorithms:WPA security algorithms focus on the encryption methods used to protect data transmitted over the Wi-Fi network. For WPA, the primary security algorithm is the Temporal Key Integrity Protocol (TKIP). TKIP was designed to improve the security of the older Wired Equivalent Privacy (WEP) standard without requiring new hardware. However, TKIP has its own limitations and vulnerabilities. Video Tutorial
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||