|
|
||
|
Imagine your phone's connection to the network as a special, secret conversation. NAS security is like a strong shield protecting this conversation. It uses secret codes to make sure only your phone and the network can understand each other. It's like having a special language that no one else knows! This shield also has watchful guards that look out for anything strange or dangerous. They check if someone is trying to listen in on your conversation or pretend to be your phone. They also make sure no one can break the connection and stop you from making calls or using the internet. This shield is always getting stronger. It's like getting regular updates to fix any weaknesses and protect against new dangers. This includes stopping bad people from blocking your connection and making sure no one can sneak into the network and cause trouble. Simply put, NAS security keeps your connection safe and private. It's like a hidden protector that makes sure you can use your phone without worrying about anyone interfering or stealing your information. It's always working in the background to keep your mobile conversations secure.
Key Components of NAS Security FrameworkNAS Security framework is built upon key components, including mutual authentication, encryption, integrity protection, and replay attack mitigation. Through mechanisms such as key derivation, security mode procedures, and algorithm selection, NAS security establishes a reliable and secure environment for signaling communication. By integrating these components, the NAS security framework ensures seamless, secure, and resilient operations, even in complex network scenarios, making it a cornerstone of modern mobile network architecture. Think of NAS security as a strong building with special features to keep it safe. First, it has a special door lock where both you and the building need to show the right key to open it, making sure only the right people can get in. Then, it uses a secret code that scrambles messages so no one else can understand them, like whispering secrets that only your friend can hear. It also has a special seal that makes sure no one has tampered with a message. If the seal is broken, you know something is wrong. Finally, it stops bad people from recording a message and playing it back later to try and trick the system. It's like checking if a message is fresh and hasn't been used before. To build this secure building, they use special tools. They create strong, unique keys from a secret password, like making many different keys from one master key. They also have rules that decide how the security features will work together, like a plan that everyone follows to stay safe. And they choose the best tools for the job, like picking the right lock for your door or the best code for your secret message. By putting all these parts together, NAS security makes sure your connection is safe and strong, even if things get complicated. It's like a reliable fortress that protects your mobile conversations, making it a vital part of how mobile networks work today. Objective of NAS SecurityNAS security is like a bodyguard for your phone's conversations with the network. It's there to protect those important messages from prying eyes and make sure nobody can tamper with them. Think of it as keeping your conversations private and ensuring that they reach the intended recipient without any changes or interference. This protection is crucial because these messages control your connection and allow you to use your phone safely. The primary goal of NAS security is to:
Key NAS Security FeaturesTo achieve its goal, NAS security has some powerful tools at its disposal. It's like a multi-layered security system. First, it checks the ID of both your phone and the network, like a bouncer at a club making sure everyone is who they say they are. Then, it puts a tamper-proof seal on messages to ensure they haven't been altered in transit, like a special package that shows if it's been opened. It also uses secret codes to scramble messages, making them unreadable to anyone trying to eavesdrop, like whispering secrets in a crowded room. Finally, it has a system to spot and reject any old messages that might be replayed by attackers, preventing them from causing trouble. NAS security provides:
Security Context EstablishmentSetting up this secure connection is like a carefully choreographed dance between your phone and the network. It starts with a shared secret, like a password known only to them. This secret is used to create special keys, like different keys for different doors in a house. Then, they exchange secret handshakes to confirm each other's identity, making sure they are who they claim to be. Finally, they use this shared secret and their handshakes to create even more specialized keys, like separate keys for a safe or a secret box. These keys are used to protect the messages and keep them confidential. The NAS security context is established as part of the EPS/5G-AKA (Authentication and Key Agreement) procedure:
Security Algorithm SelectionIt's like choosing the right tools for the job. Your phone tells the network what kind of security locks and codes it can handle. Then, the network picks the best combination from those options, considering its own security rules. Think of it as choosing between different types of locks and keys – some might be simpler, while others are more advanced. The goal is to find the most secure option that both your phone and the network can use. This selection is done during NAS security setup as follows:
NAS Security ModesImagine NAS security having two different levels of protection. At first, when your phone is just connecting to the network, it's like talking in a public place where anyone could listen. This is called "plaintext mode." But once the connection is secured, it's like switching to a private, encrypted chat where no one can understand your conversation. This is "ciphered mode," where messages are protected with secret codes and tamper-proof seals. NAS security operates in two main modes:
NAS Security ProceduresThink of it as a security handshake. The network sends a command to your phone, like saying, "Okay, let's switch to our secret code language now." This command tells your phone which codes to use for protection. Then, your phone confirms that it's ready and starts speaking in the secret language. It's like saying, "Got it, I'm now using the codes." And if at any point they realize they're not on the same page, they have a way to reset and make sure they're both using the same secret codes, like checking in with each other to make sure they're still speaking the same language. This keeps the conversation secure even if there's a hiccup along the way.
Key Lifecycle ManagementJust like you might change your passwords regularly, NAS security also refreshes the secret keys used to protect your connection. It's like changing the locks on your house to keep it secure. This happens from time to time, or when you move between different cell towers, kind of like getting new keys when you move to a new place. And just like you wouldn't leave your old keys lying around, the network securely deletes the old keys to prevent anyone from using them. This ensures that your conversations stay protected even if someone gets hold of an old key. NAS security includes mechanisms for the followings
Attack MitigationNAS security is like a vigilant guard, always on the lookout for potential threats. To prevent bad guys from reusing old messages, it uses special counters, like numbered tickets, to make sure each message is unique and hasn't been used before. This stops replay attacks, where someone tries to trick the system by repeating an old message. To prevent someone from impersonating the network or your phone, NAS security uses that "security handshake" we talked about earlier, where both sides confirm each other's identity. This stops man-in-the-middle attacks, where someone tries to sneak into the conversation and pretend to be one of the parties. Finally, to prevent eavesdropping, NAS security uses those secret codes to scramble the messages, making them unreadable to anyone trying to listen in. It's like having a private conversation in a crowded room, where only you and the other person can understand what's being said. NAS security defends against:
Interworking with Other LayersThink of it as teamwork between different security guards. NAS security protects the control center, making sure the overall connection is safe. But there's another team, called AS security, that focuses on protecting the actual data you send and receive, like your messages, pictures, and videos. They work together like different parts of a security system in a building. NAS security is like the guards at the front door and the security cameras monitoring the hallways, while AS security is like the locks on your individual office doors and the safes inside. By working together, they ensure that everything is protected, from the control center to the individual pieces of information being exchanged. This creates a secure path for all your communication, like a secure tunnel protecting everything that travels through it.
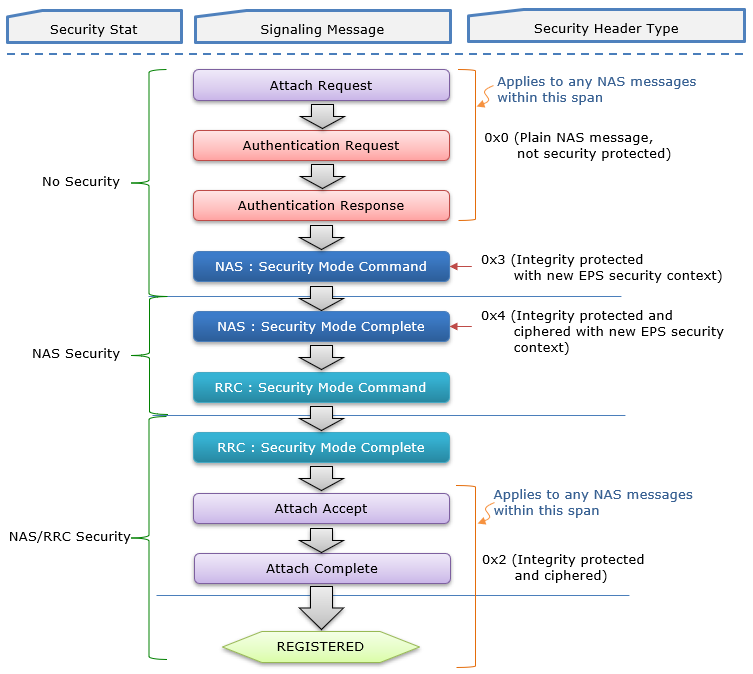
NAS Signaling Messages in Security FrameworkThere are a few critical NAS signaling message related to configure various NAS Security parameters and control the process. These messages are like special commands and confirmations that go back and forth to set things up and keep everything running smoothly. Think of them as the key pieces of a puzzle that fit together to create a secure connection. They tell the phone and the network what to do, how to behave, and what security measures to use. Without these specific messages, the whole system wouldn't be able to function securely. It's like having a secret language with specific code words that trigger different actions. Each message has a unique role to play in establishing and maintaining the secure connection, ensuring that everyone is on the same page and following the right procedures. Those messages handle things like verifying identities, similar to exchanging code words to make sure they're talking to the right person. They also set up the security level and choose the right "secret codes" to use, like agreeing on which cipher to use for their encrypted messages. Additionally, they manage the creation, updating, and deletion of those secret keys, similar to exchanging keys to a safe house and changing them regularly. These messages are crucial for establishing and managing the secure channel, ensuring that only authorized parties can access the information and that it remains confidential and tamper-proof. They're like the behind-the-scenes communication that sets the stage for a secure operation.
These messages in the context of overall signaling procedure can be illustrated as below (in case of LTE. NR is almost same except small difference in security header type)
Reference :
|
||