|
|
||
|
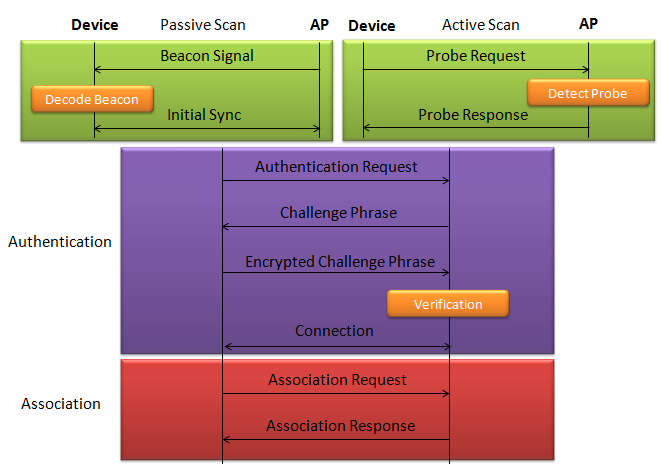
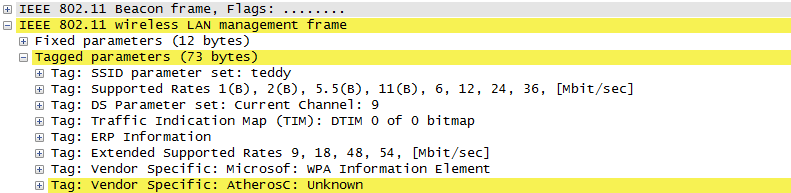
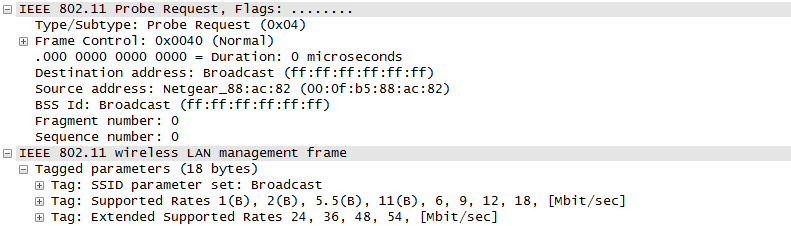
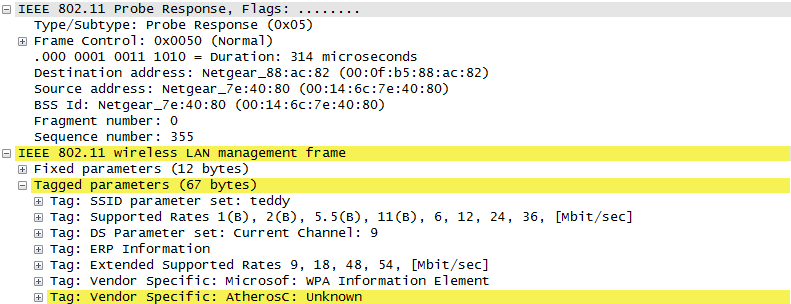
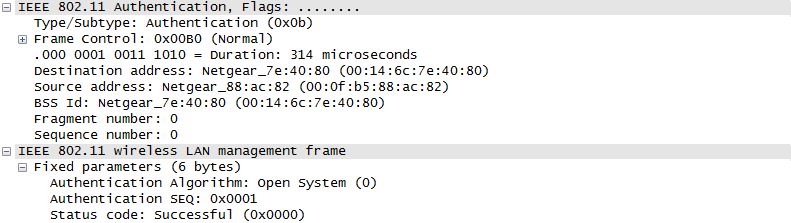
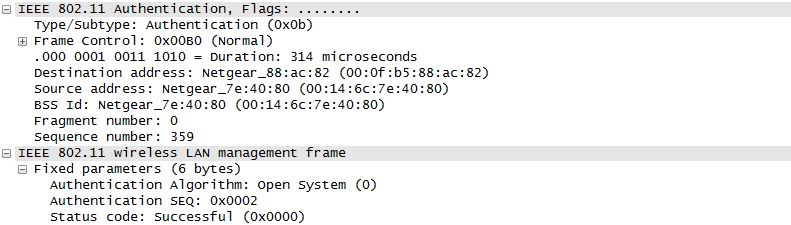
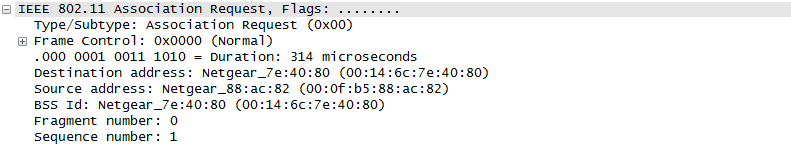
ProtocolThere are a couple of different mode of WLAN operation. Following is the protocol sequence for the case we commonly use where we have an AP(Access Point) and the Device(client PC or Smart phone WLAN) gets connected to the access point. Overall ProcedureThe AP is periodically transmitting (broadcasting) a special signal called Beacon signal saying "I am here.. I am here .. I am capable of this and that .. etc)". Basically this Beacon is like MIB/SIB + Physical Layer Sync channel in mobile communication (e.g, WCDMA/LTE etc). AP broadcast this Beacon several times per seconds. Beacon transmission interval is contained in one of Beacon information fields. (See Beacon data field) When you turn on WLAN on your PC or Smart phone, the device first detect and decode this beacon signal and establish physical synchronization. After the physical Sync get established, the device and WLAN network goes through the authentication process and then association process which is similar concept to the registration process in mobile phone communication. Speaking of scanning, there are two types of scanning. One is called Passive Scan and the other one is called Active Scan. As shown below, in Passive Scan the device scans and detect Beacon signal from AP and establish the sync based on the Beacon signal. In Active Scan mode, device broadcast Probe Request to all the APs (or any specific AP), if there is any AP that detect the probe request, it sends Probe Response to the device.
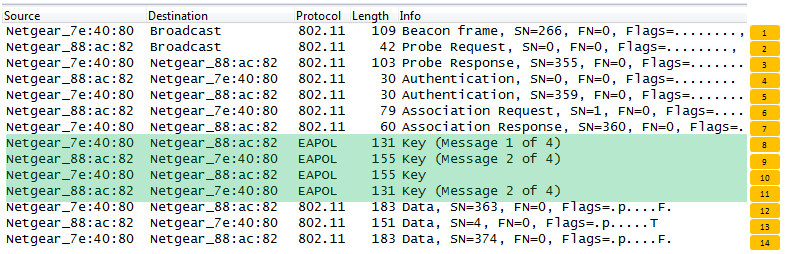
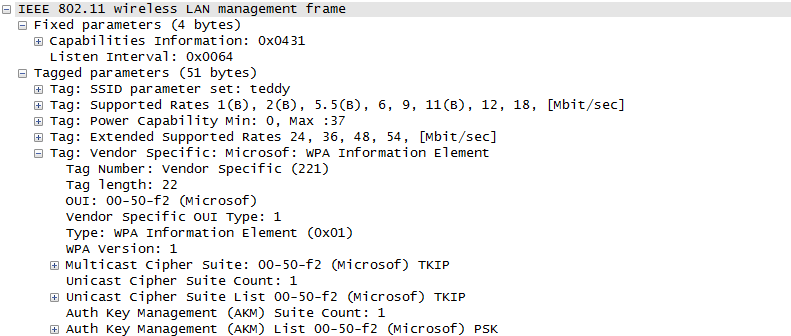
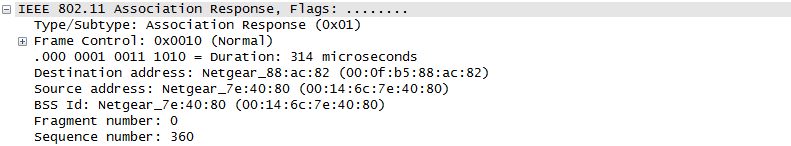
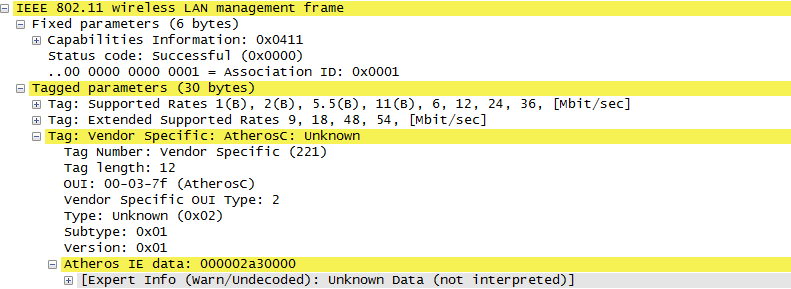
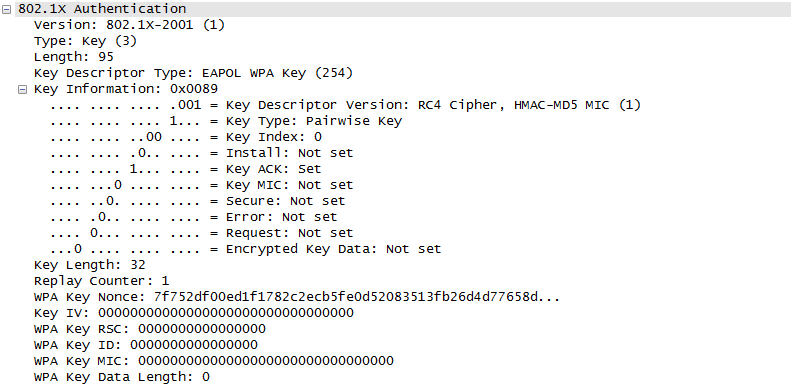
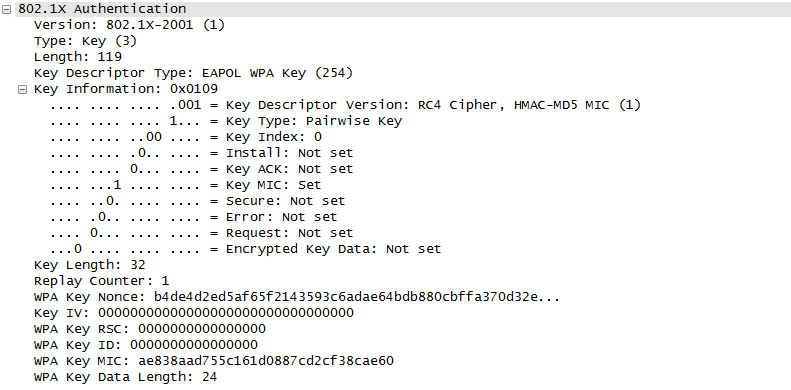
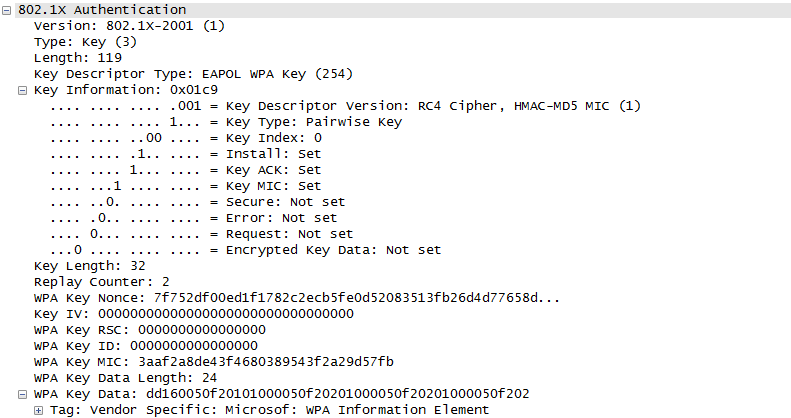
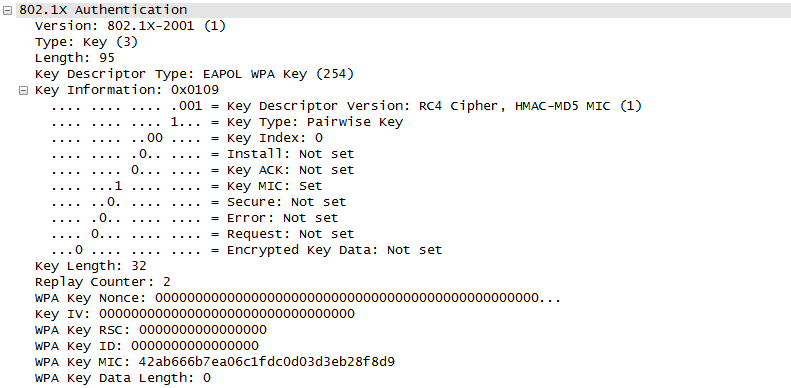
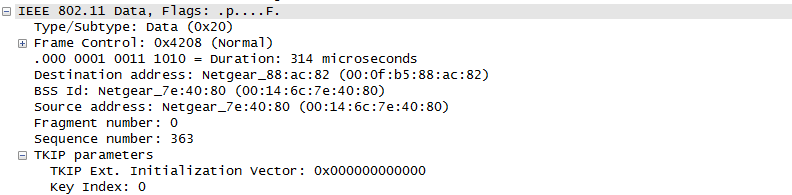
Once they went through Authentication and Association process, now the device can send and receive user data. Here comes a tricky issues for packet transaction especially when a party tries to transmit something. WLAN does not have concept of dedicated channel (e.g, as in UMTS mobile communication) and it does not have any well designed physical/MAC layer scheduing for each separate user. Basically they are allowed to transmit anytime they like, but in reality a device cannot transmit any time. If it transmit some data while another device is sending data, the data may get lost in the air or it would cause the data for other device get lost since the transmission from the two device would interfer each other. We need some special technique to prevent this problem happening. In Wired LAN, we use a techniq called CSMA/CD and in WLAN we use another technique called CSMA/CA. For the details of these technique, i will write a separate section.. but the goal/purpose of the technique is to make it sure that a device transmit the data when no other device is transmitting anything. The trace log shown here came from Aircrack-NG Tutorial: WPA Packet Capture Explained. In general, Step (1)~(7) is common to most of WLAN attach process, but the steps after this would be different depending on the security option you set on the device and access point. (Refer to ePDG protocol sequence if you want to see an examples that is different from the step (8) and later)
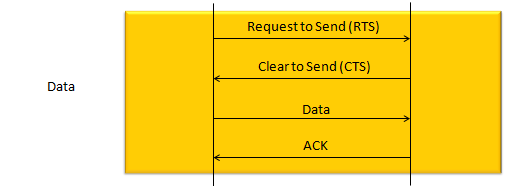
The techniqu that WLAN is using to transmit data without interfering other's is as shown below. The concept is simple. a device (let's call this a source device) send a short signal called RTS to another device (let's call this a destination device). If destination device successfully got the RTS, it is supposed to send CTS. If the source device successfully detect/decode the CTS, it transmit the main data. if the data is successfully recieved/decoded by the destication device, the destination device send 'ACK'. For each and every packet transmission, this process repeats.
Data Transmission in DetailOnce the initial connection setup is completed by the procedure that is explained in previous section, usually the procedure for user data flow starts. In this section, I will go over how the user data flow goes on. First case is where a chunk of user data is transmitted in single transmission as illustrated below.
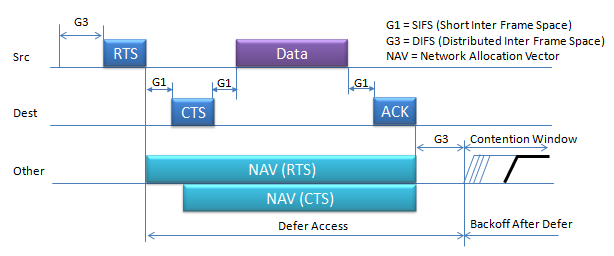
More detailed process of this data tranmission in terms of timing can be illustrated as shown below.
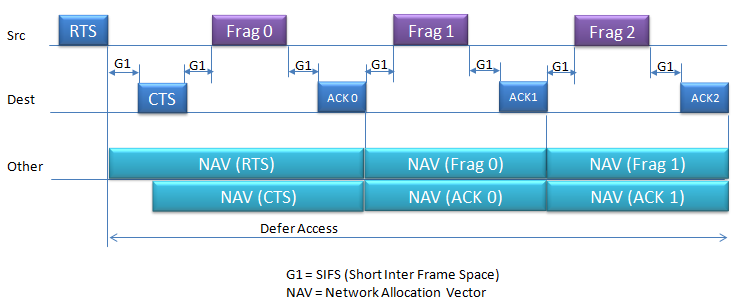
When data packets are larger than the network's Maximum Transmission Unit (MTU) or when the network conditions are such that sending smaller packets is more reliable.Fragmentation in Wi-Fi networks happens. In case of Fragmented Frame, the sequence goes as follows :
It is a short inter frame space that usually happens in some situation as below.
Fragmentation in Wi-Fi networks happens when data packets are larger than the network's Maximum Transmission Unit (MTU) or when the network conditions are such that sending smaller packets is more reliable. The decision to fragment is typically made by the device's network stack, which takes into account the current network conditions, the capabilities and settings of the network devices, and the size of the data being sent.
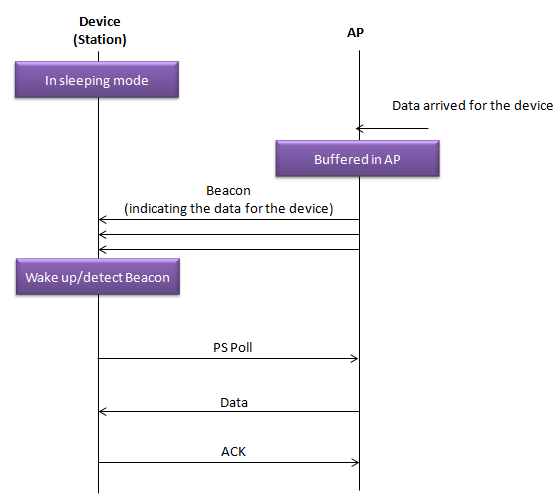
Sleeping Mode and Data TransmissionThe sequence diagram shown bellow illustrate how a Wi-Fi-enabled device (Station) in power-saving mode communicates with an Access Point (AP) to receive data. This process ensures that devices on a Wi-Fi network can conserve power by sleeping and only waking when necessary to receive data.
Here’s a step-by-step explanation of what’s happening:
Reference :[1] IEEE 802.11 - Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications
|
||